- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Requirements
- Configure Symantec Endpoint Protection for use wit...
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
05-18-2016
08:30 PM
- edited on
08-04-2023
08:20 PM
by
sophie
![]()
To pull data from the Linux, Unix, Mac and Windows computers, VMware servers and other devices in your network, Lansweeper queries a number of ports on the devices. A list of scanned ports can be found in this knowledge base article. It is important to allow traffic from your Lansweeper server to these ports, to ensure a successful network scan.
Since the release of Lansweeper 6.0, Symantec Endpoint Protection in particular is prone to wrongly identifying Lansweeper traffic as port attacks on your devices. This may result in traffic being blocked and errors similar to the one below in your Symantec installation. Lansweeper 6.0 scans the same network device ports as previous Lansweeper releases, but does so more quickly to speed up scanning. Symantec identifies this sped up traffic as port attacks in some cases.
An easy way to prevent errors like the one below and to allow for a successful network scan is to whitelist all traffic coming from your Lansweeper server. More restrictive rules may work as well.
Whitelisting all Lansweeper traffic
To whitelist all traffic from the Lansweeper server in Symantec Endpoint Protection, do the following:
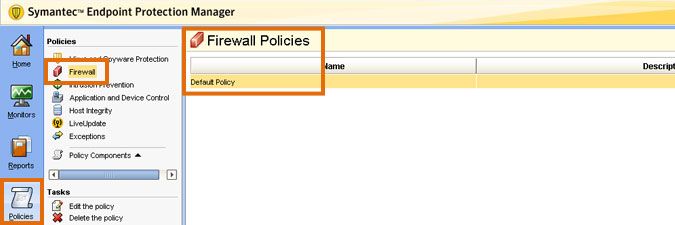
- Open Symantec Endpoint Protection Manager.
- Select the Policies tab.
- Select the Firewall tab.
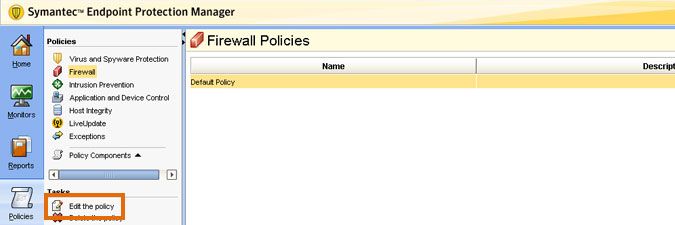
- Select the existing policy applied to your client machines on the right and choose Edit the policy. Alternatively, create a new policy to apply to your clients.
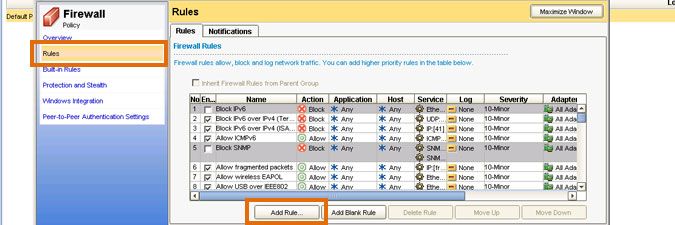
- In the policy pop-up, select the Rules tab.
- Select the Add Rule... button.
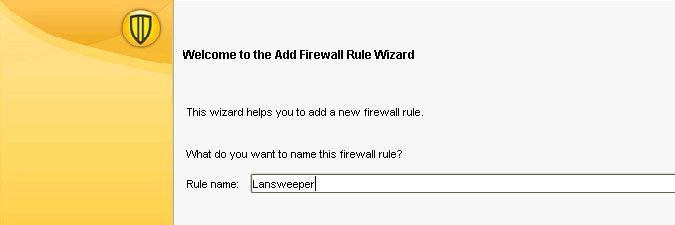
- Give your rule a name, e.g. "Lansweeper". Select Next to continue.
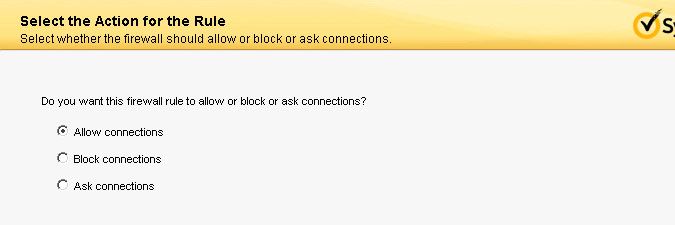
- Tick Allow connections. Select Next to continue.
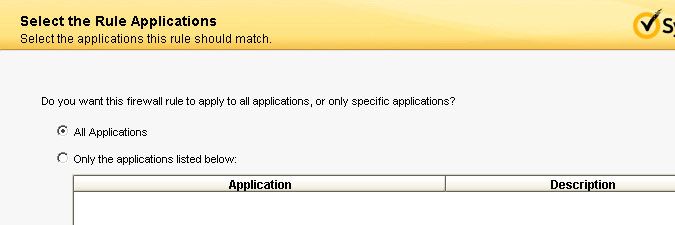
- Tick All Applications. Select Next to continue.
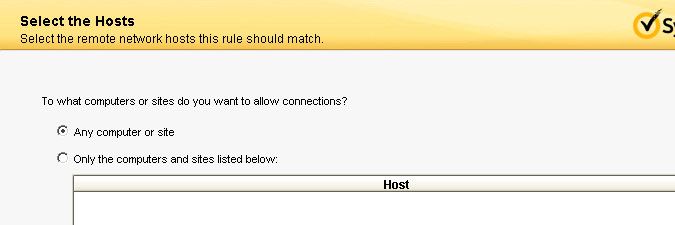
- Tick Any computer or site. Select Next to continue.
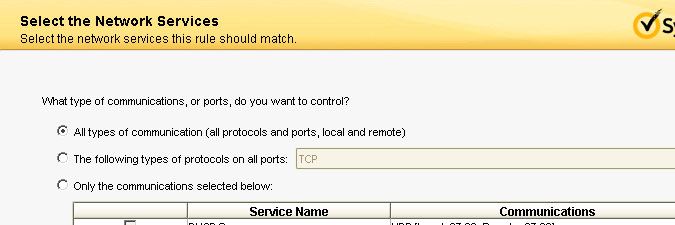
- Tick All types of communication (all protocols and ports, local and remote). Select Next to continue.
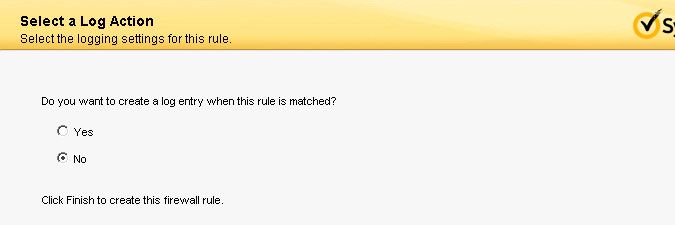
- Optionally, you can choose to have a log entry generated when a connection is made by the Lansweeper server. Select Finish to create the rule.
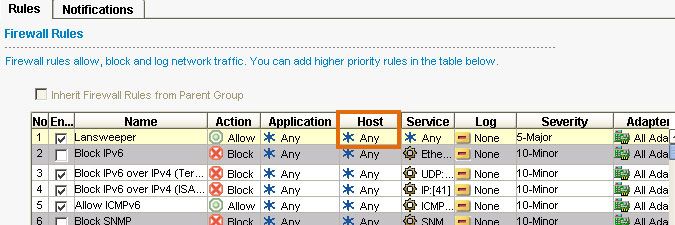
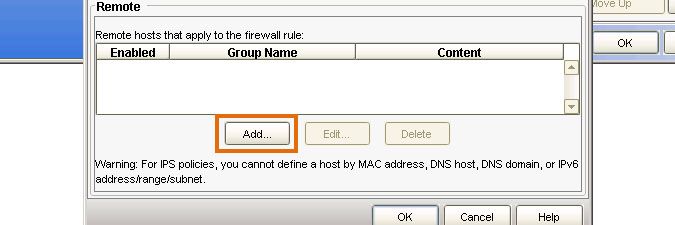
- Once the rule has been created, double-click in the Host column and submit your Lansweeper server's IP address, to only apply the rule to traffic coming from your Lansweeper server.
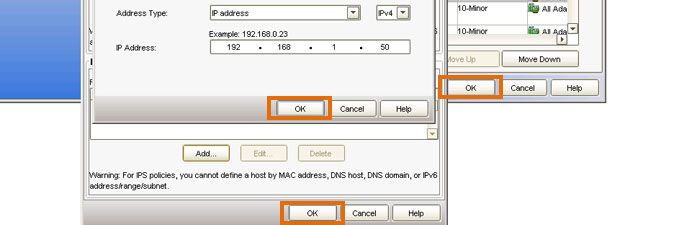
In the example below, the IP address of the Lansweeper server is 192.168.1.50. Select OK several times to close all pop-ups and submit your changes.
Was this post helpful? Select Yes or No below!
Did you have a similar issue and a different solution? Or did you not find the information you needed? Create a post in our Community Forum for your fellow IT Heroes!
More questions? Browse our Quick Tech Solutions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now