- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Cyber Security and Risk Insights
- Create vulnerability prioritization rules
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This documentation is for the old UI. For documentation for the new preview UI, Knowledge Base - Preview UI.
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-12-2024 02:18 PM - edited 11-04-2024 11:55 AM
This page provides information on how to view and manage vulnerabilities in Lansweeper's Risk Insights, including creating custom and advanced filter views, and provides a couple of practical use cases.
When you have a high number of vulnerabilities, it’s crucial that you create a prioritization strategy. Your list of vulnerabilities is filtered by confidence level by default. This means the list will only display Common Vulnerabilities and Exposures (CVEs) with a High confidence level. For more information about confidence level, see Confidence level.
You can also customize your list of vulnerabilities to fit your needs, based on:
- Asset type
- Number of CVEs affecting an asset
- CVSS Base Metrics
- Affected products
- Availability of patches
- Availability of exploits
and much more!
In this article, we’ll go over how you can create custom views or advanced filters to customize your list of vulnerabilities, and we’ll illustrate this with a few practical use cases.
Create a custom view
Organize your list of active vulnerabilities to best suit your unique environment by creating custom views. Custom views allow you to create a personalized view of your data by displaying the information you require in the format your desire.
- In Risk Insights > Active vulnerabilities or Vulnerable assets, select Customize view.
- Under Fixed columns, toggle the fixed columns that you want to display On or Off. Select and hold the column to reorder it.
- Under Scrollable columns, hover over a column and select X to remove it, or select and hold the column to reorder it.
- Under Available columns, use the search to find the column you want to add, then click to add it to your custom view.
- Select Apply.
- If you're happy with the view, select Unsaved View > Save view and configurations. If you'd like to revert to the previous view, select Restore the default view.
- Enter a name for your view. You can also add a description.
- Select Save.
Your view is added to Risk Insights > Custom views.
Create an advanced filter view
Your list of vulnerabilities is filtered by a high confidence level by default, but you can create advanced filters to discover specific data.
- In Risk Insights > Active vulnerabilities or Vulnerable assets, select Advanced filter view.
- Select + to add additional filters.
- Enter a field name or select the arrow to view a list of options.
- Select an operation.
- Enter a value.
- Select Apply.
- If you're happy with the view, select Unsaved view > Save view and configurations. If you'd like to revert to the previous view, select Restore the default view.
- Enter a name for your view. You can also add a description.
- Select Save.
Use cases: prioritization scenarios
After learning how you can customize your list of vulnerabilities, browse through some practical use cases that demonstrate how you might use custom views in Risk Insights to filter for exploitable vulnerabilities.
Create rules for specific environments
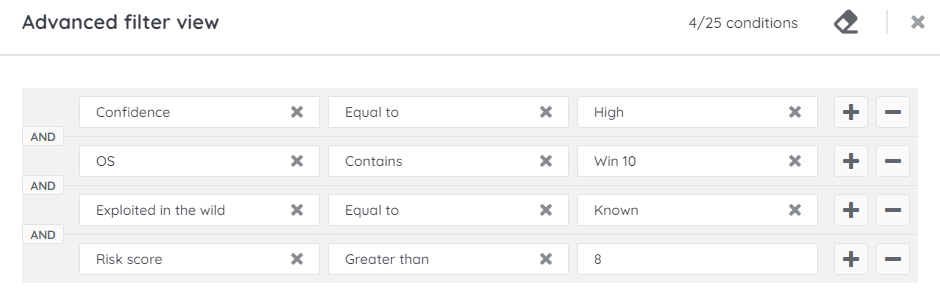
Let’s start off with a use case demonstrating how you might prioritize your list of active vulnerabilities for a Windows estate.
- Go to Risk Insights > Active vulnerabilities and select Advanced filter view.
- Select + to add additional filters.
- Add the following fields:
- OS – Contains – Win 10
- Exploited in the wild – Equal to – Known
- Risk score – Greater than – 8
- Select Apply.
- Optionally, sort your vulnerabilities by Severity.
- Select Unsaved view > Save view and configurations.
- Give your view a name. In this case, we’ll call it Windows estate.
- Optionally add a description.
- Select Save.
Create rules for specific locations
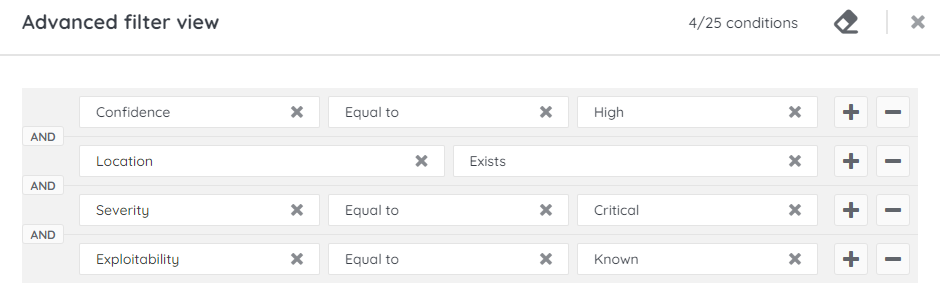
Next, we'll take a closer look at a scenario for prioritizing your vulnerable assets based on their location.
- Go to Risk Insights > Vulnerable assets and select Advanced filter view.
- Select + to add additional filters.
- Add the following fields:
- Location – Exists
- Severity – Equal to – Critical
- Exploitability – Equal to – Known
- Select Apply.
- Select Unsaved view > Save view and configurations.
- Give your view a name. In this case, we’ll call it Location overview.
- Optionally add a description.
- Select Save.
Create a rule for the entire estate
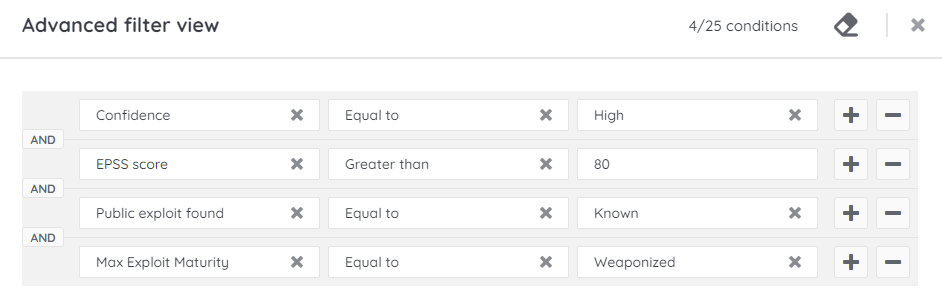
Let's examine another scenario showing how to prioritize your list of active vulnerabilities for your entire estate.
- Go to Risk Insights > Active vulnerabilities and select Advanced filter view.
- Select + to add additional filters.
- Add the following fields:
- EPSS score – Greater than – 80
- Public exploit found – Equal to – Known
- Max Exploit Maturity – Equal to – Weaponized
- Select Apply.
- Select Unsaved view > Save view and configurations.
- Give your view a name. In this case, we’ll call it Generic priority.
- Optionally add a description.
- Select Save.
Create rules based on priorities
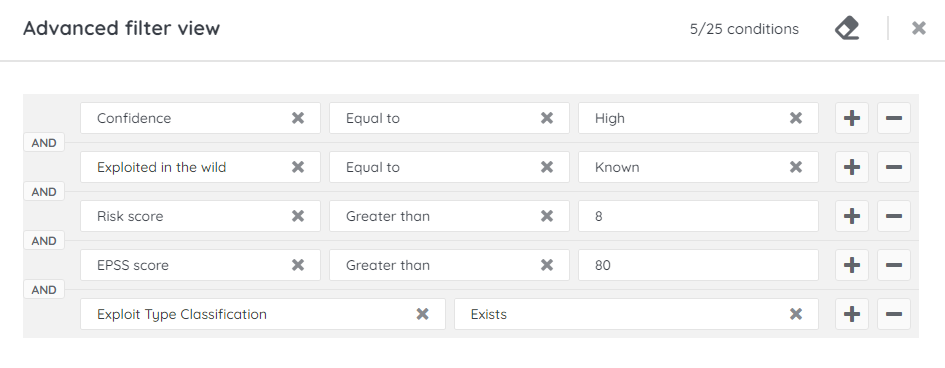
Finally, let’s consider a practical example of prioritizing active vulnerabilities by priority buckets.
- Go to Risk Insights > Active vulnerabilities and select Advanced filter view.
- Select + to add additional filters.
- Add the following fields:
- Exploited in the wild – Equal to – Known
- Risk score – Greater than – 8
- EPSS score – Greater than – 80
- Exploit Type Classification – Exists
- Select Apply.
- Optionally, sort your vulnerabilities by Updated on.
- Select Unsaved view > Save view and configurations.
- Give your view a name. In this case, we’ll call it Our critical issues.
- Optionally add a description.
- Select Save.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now