- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Cyber Security and Risk Insights
- Customize the list of vulnerabilities
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This documentation is for the old UI. For documentation for the new preview UI, Knowledge Base - Preview UI.
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-30-2023 02:52 PM - edited 06-20-2024 11:55 AM
This page explains how to create and manage custom views in Risk Insights to filter unnecessary information.
As cybersecurity gains importance by the day, an organized list of the vulnerabilities affecting your devices becomes a crucial tool in any security officer’s arsenal.
Since more and more vulnerabilities are discovered, the list of Active vulnerabilities tends to grow as well. The Custom views feature allows you to filter unnecessary information from these views and select the data you want to examine further, covering your analytical needs.
With custom views, you can:
- Create a custom view
- Sort by multiple columns
- Create an advanced filter view
- Manage a custom view
- Export a view
Create a custom view
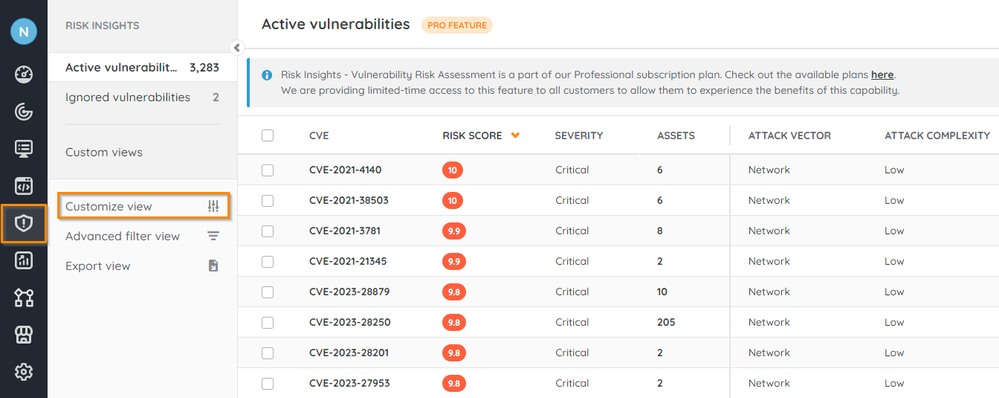
- Go to Risk Insights > Active vulnerabilities, and select Customize view.
- Under Fixed columns, toggle the fixed columns that you want to display On or Off.
- Under Scrollable columns, hover over a column and select X to remove it, or select and hold the column to reorder it.
- Under Available columns, use the search to find the column you want to add, then click to add it to your custom view.
- Select Apply.
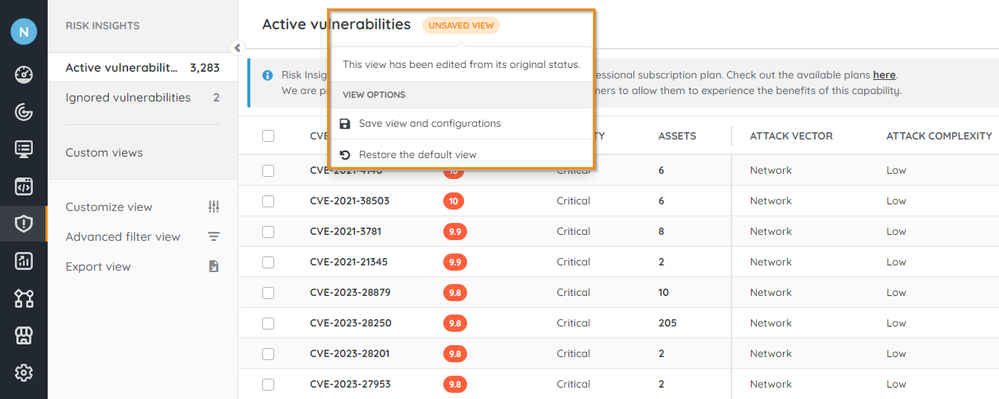
- If you're happy with the view, select Unsaved View > Save view and configurations. If you'd like to revert to the previous view, select Restore the default value.
- Enter a name for your view. You can also add a description.
- Select Save.
Your view is added to Risk Insights > Custom view.
Sort by multiple columns
- Go to Risk insights > Active vulnerabilities.
- Select a second column you want to sort vulnerabilities by. Vulnerabilities are sorted by Risk score by default.
- Optionally, select more columns to sort your list of vulnerabilities by. You can sort vulnerabilities by up to 4 different columns at the same time.
Your list of vulnerabilities will be sorted by the selected columns, prioritizing those selected first. - Select Unsaved View > Save view and Configurations.
- Enter a name for your view. You can also add a description.
- Select Save.
You can remove a sorted column by selecting X.
Create an advanced filter view
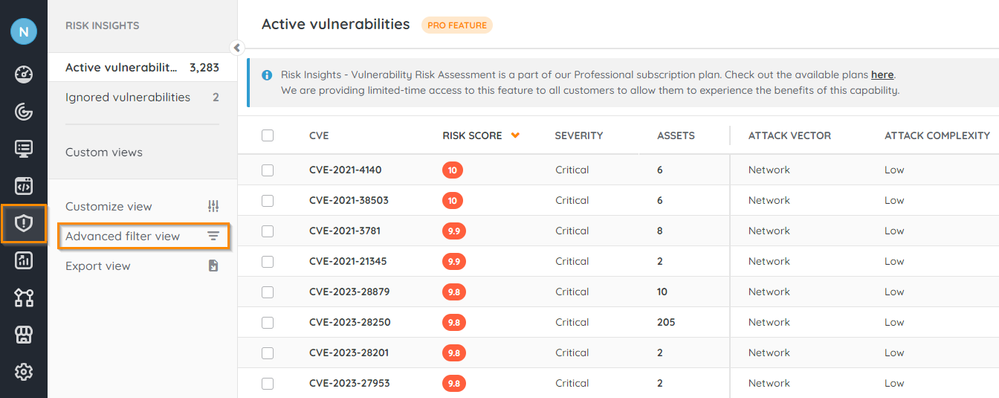
- Go to Risk Insights > Active vulnerabilities, and select Advanced filter view.
- Type in a field name or select the arrow to view a list of options.
- Select an operation.
- Enter a value. Either:
- Choose from the list of predefined values.
- Create new values by selecting Change. Enter your value then select Add filter value if you wish to add additional values, and select Apply values once you're done.
- Select + to add additional filters.
- Select Apply.
- If you're happy with the view, select Unsaved View > Save view and configurations. If you'd like to revert to the previous view, select Restore the default value.
- Enter a name for your view. You can also add a description.
- Select Save.
Your view is added to Risk Insights > Custom view.
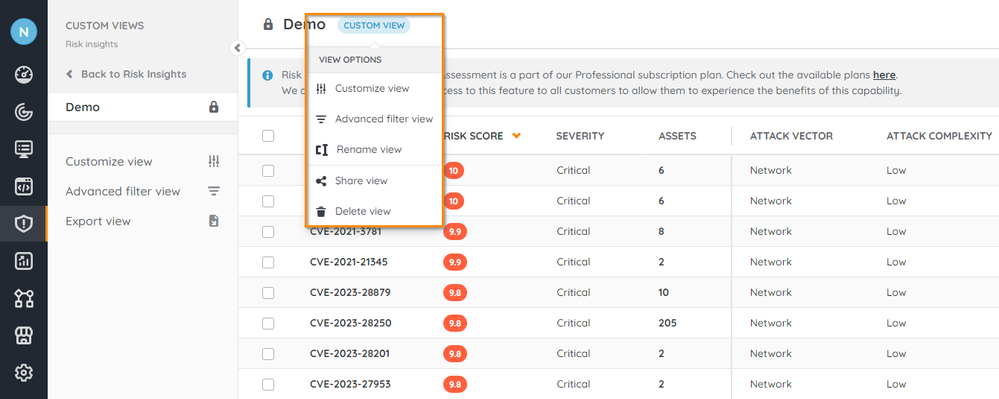
Manage a custom view
- Go to Risk Insights > Active vulnerabilities, and select Custom views.
- Select the view you wish to edit.
- Select Custom view. From there, you have a variety of options to manage the custom view.
Export a view
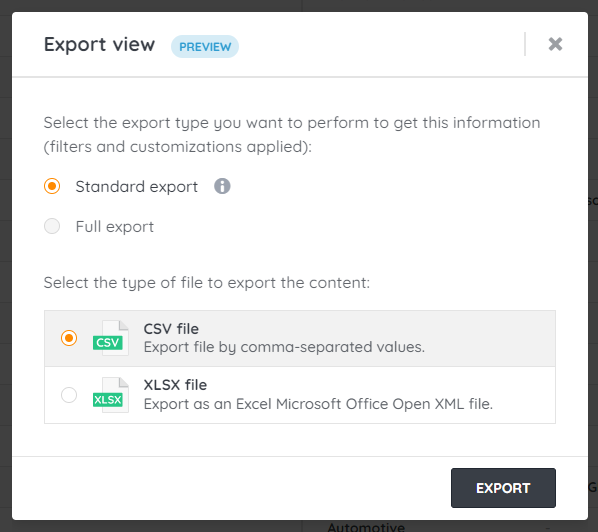
- Go to Risk Insights > Active vulnerabilities, and select Export view.
- Select the export type:
- Standard export: Download the first 10,000 results automatically. Your file will start downloading once you select Export.
- Full export: Download all of the results. You'll receive an email with the attached file once you select Export.
- Select CSV file or XSLX file for the file type.
- Select Export.
Was this post helpful? Select Yes or No below!
Did you have a similar issue and a different solution? Or did you not find the information you needed? Create a post in our Community Forum for your fellow IT Heroes!
More questions? Browse our Quick Tech Solutions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now