- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2023 10:45 PM - last edited on 03-31-2024 03:20 PM by Mercedes_O
Hello,
Trying to configure a new Active Directory User/Group Path scanning target.
After I fill in the required information (Scanning Type, Asdi Path, Domain & Description) and click OK, the window closes and it does not create a new scanning target. I can tell because the list of total scan targets does not change, I have also tried filtering for all Active Directory User/Group Path scanning targets and none appear.
Any advice is appreciated.
Solved! Go to Solution.
- Labels:
-
Built-In Reports
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 07:54 PM
Lansweeper support has confirmed that this is a known bug, with no ETA on a fix.
Thanks for your help @jduke_halls , I appreciate your quick responses!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2023 05:18 AM
Oh, LS 11.1 is very buggy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 07:54 PM
Lansweeper support has confirmed that this is a known bug, with no ETA on a fix.
Thanks for your help @jduke_halls , I appreciate your quick responses!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2023 10:59 PM
If you haven't already, you're also going to want to set up an "Active Directory Domain" scan target: https://community.lansweeper.com/t5/scanning-your-network/scan-an-active-directory-domain-scanning-t.... You won't need to add the OU filters to the AD scan itself, since you already have the other scan for the User/Group Path.
If you're on-prem AD Scanning, I recommend setting up a preferred Domain Controller and LDAPS for your domain. Default port for LDAPS is 636 - Best practice in Microsoft-land. It's a little beyond halfway down on your Scanning Methods page. There's even a "Test" to make sure everything is working correctly in the LDAP(S) area.
If you're using Active Directory Certificate Services to generate certs across your environment, you'll want to make sure your LanSweeper Scanning server has the ADCS CA cert that your AD generated in the Trusted Root Authorities in Certificate Management for the Computer Certificate store.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 02:17 PM
Hi there, thanks for your response
You're correct, we already have an Active Directory Domain scan target, which has been in place for a while, using on-prem AD. We also already have a preferred domain controller configured.
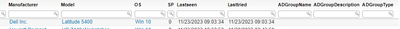
In our AD Domain scanning target, there are no OU or Site filters, so as I understand it should also be scanning AD groups?
This is the result I get when running the "Domain Computers and their AD groups" report.
It's the same for all line entries in this report, all attributes relating to AD groups are blank.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 02:39 PM
Yeah, at minimum, you should likely be getting the Domain Computers account.
In your ADSI path for your scanning target on the AD User/Group path, are you using the root of the domain being scanned (i.e. DC=subdomain,DC=sampledomain,DC=local) or are you mapping to a specific OU (i.e. OU=Network Users,DC=subdomain,DC=sampledomain,DC=local)?
If you're mapping to a specific OU, you may need to add more OUs to make sure the scanning captures all the data needed. So in the example below, Groups and Users are in separate OUs
DC=subdomain,DC=sampledomain,DC=local
├── Network Computers
│ └── # OUs for computer types
├── Network Groups
│ └── # OUs for type of groups
├── Network Users
│ └── # OUs for user types
├── Users
│ └── # Default AD location with built-in AD Groups
...In this case, if I don't go to the root level and want to capture all of my OUs, I'll have to add 4 different User/group paths to make sure that everything can be scanned and associated together
- OU=Network Computers,DC=subdomain,DC=sampledomain,DC=local
- OU=Network Groups,DC=subdomain,DC=sampledomain,DC=local
- OU=Network Users,DC=subdomain,DC=sampledomain,DC=local
- OU=Users,DC=subdomain,DC=sampledomain,DC=local
The "easy" way would be to use the root of the domain (DC=subdomain,DC=sampledomain,DC=local), but as admins, we should err toward giving scanners the least amount of privileges needed to accomplish what we're trying to do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 02:51 PM - edited 11-29-2023 02:53 PM
Hello Jduke,
Part of the issue is that when trying to set a new AD User/Group path scanning target, it just simply does not add the scanning target once the OK button is selected to create the target. I'm able to add other scanning target types no problem.
The scanning target list does a quick re-fresh after OK is pushed but the total number of targets does not go up, nor does the target get added to the list. I had presumed this was because we are already scanning for AD groups using the AD Domain scanning target type.
I've tried adding the specific ADSI path to the OUs I want scanned using the AD User/Group target type, as well as simply the root to the domain as the ADSI path, but both paths refuse to take, and the same behavior is observed where the new scanning target is not added.
Thanks for your help with this, it's really appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 03:47 PM
The behavior of saying it's in the scanning queue and not being there on the AD User path is normal. Also, just to make sure, when you scan your AD paths, did you enable the scanning interval? Are you logging Active Directory security events to a SIEM and can you see the activity from your LanSweeper server?
If those are all good, it sounds like it could be a bug. I know that since version 11 came out with the new scanning engine that there have been some issues with AD Scanning.
We had a major issue where we turned off the LanSweeper server/scanner on 11.1.1.3. After the update to 11.1.2.1, we don't seem to have any problems currently with the AD side of things.
We'll likely be updating to 11.1.3.0 sometime soon, just a little twitchy about updating after the 11.1.1.3 debacle.
If you want to engage LanSweeper support in this: https://www.lansweeper.com/contact-support/. They have a couple things that will help them diagnose (screenshots, video, gatherlogs) listed on the page that will hopefully get you an answer as to what's happening.