- Lansweeper Community
- Forums
- Product Discussions
- Re: New Preview Capability - Security Vulnerabilit...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2022 10:11 AM - last edited on 06-14-2023 08:04 PM by Mercedes_O
Lansweeper is delighted to announce new capabilities in the security vulnerabilities space. Building on the foundations of our world-class scanning technology Lansweeper has enhanced our software scanning to normalize and enrich with NIST standard naming and identification. This enables Lansweeper to offer value add capabilities matching clients' software against NIST vulnerabilities databases.
This is a preview feature and will be iterated frequently over the next few months before the official release. Please use this space to give suggestions +ve or -ve to help us improve the product.
- Labels:
-
Vulnerability Risk Assessment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2023 09:06 AM
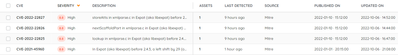
Hi, I just set up a new environment to test the vulnerability insights. What I see is a list of detected vulnerabilities but I would add a column with where this is detected what product and what machine. I see filtering is requested and I agree to that too. The overview currently is hard to use. From this overview it should be clear what component, or peace of software should be updated.
Both machines are Windows machines.
Any idea when software lifecycle information is added?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2023 09:11 AM
Only sofyware running on this machine is
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2023 07:15 PM
This seems like a cool feature. I have a couple questions. I apologize in advance if these have been answered, I just want to add my own experience.
1) In the Security Insights Page, I'm only able to sort on the severity of the CVE. It would be nice to sort on any column. Specifically the "Source" or "Assets" column. I'm sure this is actively being implemented.
2) I would like to know how often each CVE is scanned on an asset. For example, I updated an application that was affected on one of my assets. I performed a rescan on my local lansweeper server. No update yet on the cloud portal. I also forced a re-sync on the asset. No change so far either. On a side note, I'm wondering if there is way to view the status of re-syncing an asset(s) so I can rule this out as an issue?
Overall, I look forward to seeing how far this feature goes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2023 05:58 PM
Hi @whoami ,
1) You can also sort by CVE-ID, Last detected, or Updated On, but, indeed, some columns are not available. However, after releasing the custom views next week, you will be able to customize the displayed columns and sort them as well. 🙂
2) The vulnerabilities calculation is not tied to the scanning process, meaning if you rescan an asset, their vulnerabilities are not recalculated at that moment. For each vulnerability, the Last detected field is available, which indicates the last time the vulnerability was recalculated against your inventory assets. Currently, there are different schedules based on severity. For example, Critical ones of the last year are calculated four times a day, HIGHs from last year are once a day,... I am glad to say we are working on improvements for our vulnerability engine, which will basically allow refreshing the info in real time.
Thanks, and I hope the feature covers all your future expectations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 02:51 PM
Great feature.
We do however need filtering for devices - primarily 'last seen'
eg: seen within: 7 days, 30 days, (+ custom range?)
We have 180 days data retention, so a lot of computers have been replaced, but are shown as vulnerable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2023 11:14 AM
Hi @Lars_Kruse ,
Thanks, I am glad this feature is interesting to you.
Next week we are releasing the Custom views and Advanced filtering capabilities for Sec. Insights.
Although the filtering fields available are more related to the vulnerability itself, we already included the asset state as a filter, and precisely we want to check with you the fields that would be interesting to you to be included. I will consider your suggestion of the "last seen", I think it makes sense.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2023 06:52 PM
I really like this feature. I have noticed that I am seeing a vulnerability for two of my Windows Servers and the patch that is currently available is no longer a standalone patch, it's part of cumulative update from 2020. I know these two servers are updated. Are you reporting on the latest patch available that fixes the vulnerability or just looking to see if the standalone patch has been installed?
That could lead to a lot time wasted if the issue has been patched already but Lansweeper is only looking for the standalone patch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 11:53 AM - edited 01-12-2023 11:56 AM
Hi @bpsrmorrison,
We are aware of the limitation in the current solution to detect some of the patched vulnerabilities based on the CVE configuration, including the cumulative updates you indicated above.
Improving this capability is our main focus right now, making it possible to properly match all the installed KBs with the corresponding vulnerabilities, even if it is part of a cumulative update. I will share more news on it soon.
In the meantime, I recommend reading the following post from our support team:
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2023 02:36 PM
Iv got an issue where the asset has been removed but still showing up on the list
When you got the name of the asset I get
Oops!
Asset not found
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 10:43 AM
Hi @WM ,
The asset deletion is not reflected until the vulnerability affecting it is recalculated, which, for now, means hours (depending on the severity of the vulnerability).
We are already working on getting a faster refresh of the deleted assets. However, it is not the most critical task as deleting assets is not performed as often as other actions.
Thanks
Product Discussions
Share feedback, exchange ideas and find answers to Lansweeper product questions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now- How can Lansweeper help me identify missing updates on my devices? in Technical Support Solutions
- Is it possible to integrate Lansweeper with Splunk? in Technical Support Solutions
- Lansweeper Connect Spring 2025: From Insights to Impact in General Discussions
- New Reboot & Review: CISA Verified Exploits — Why This One’s Worth Your Time in General Discussions
- Vulnerability on HTTP Security Header Not Detected in Product Discussions