- Lansweeper Community
- Forums
- Product Discussions
- Re: New Preview Capability - Security Vulnerabilit...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2022 10:11 AM - last edited on 06-14-2023 08:04 PM by Mercedes_O
Lansweeper is delighted to announce new capabilities in the security vulnerabilities space. Building on the foundations of our world-class scanning technology Lansweeper has enhanced our software scanning to normalize and enrich with NIST standard naming and identification. This enables Lansweeper to offer value add capabilities matching clients' software against NIST vulnerabilities databases.
This is a preview feature and will be iterated frequently over the next few months before the official release. Please use this space to give suggestions +ve or -ve to help us improve the product.
- Labels:
-
Vulnerability Risk Assessment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023 07:33 PM - edited 05-17-2023 07:36 PM
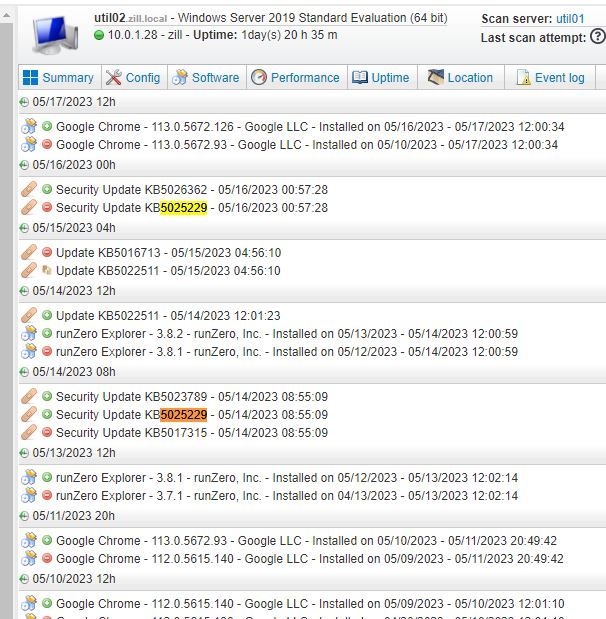
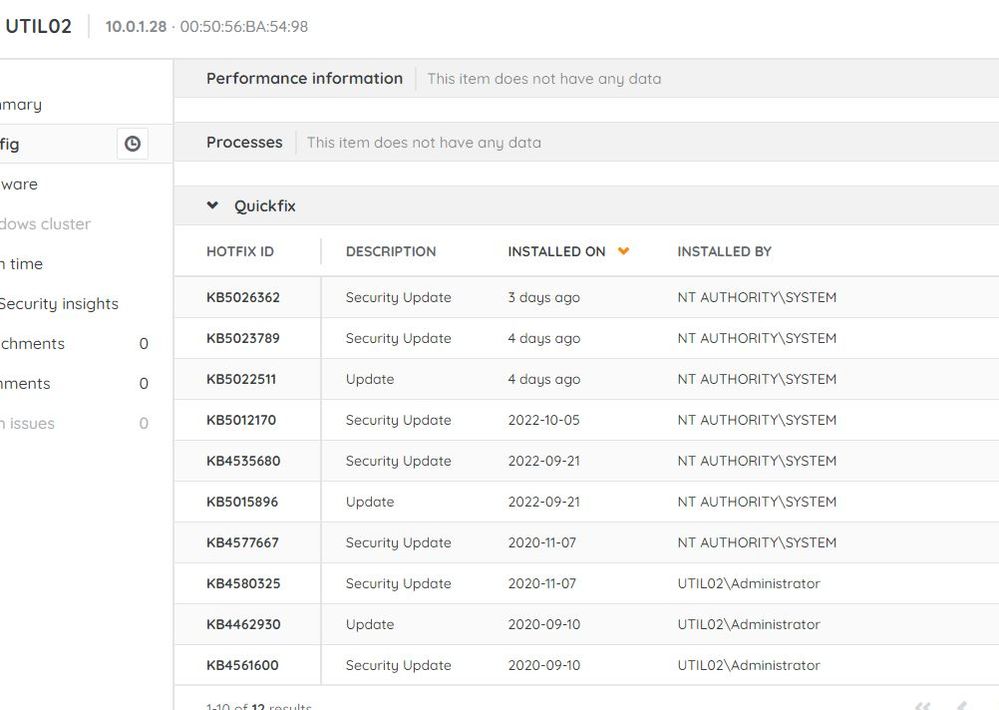
Yah... I check the insights every now and then in my lab to doublecheck them - I think* that these vulns reported don't work with supercedence/rollups - at least thats what I seem to find when I check this section of features. I did just check CVE-2023-28250 which showed a remedy of April's patch, which I didn't have installed at the time of checking, so I patched with that patch... then i patched with May's that came out recently, and it still reported as vulnerable. I did notice that on-prem had the April patch as installed, then uninstalled/May patch installed (normal behavior to see the minus sign on old patch when plus sign new patch is there) - but the cloud doesn't show the April patch as ever being installed - it just kinda goes to May's when I synced the asset. Soooooo - that leads me to believe that it 1) doesn't handle supercendence until someone on LS side/team updates the checks(??) i'm not sure... but then 2) the cloud isn't accurately reporting the quickfix history... so either one of those two scenarios could result in the report being inaccurate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2023 11:14 AM
Any near time improvement in the way vulnerabilities reports are presented with able export Asset details along with CVSS in a user friendly manner than a mannual task of looking in to each CVSS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2023 02:02 PM
Is there a way to Ignore an asset from vulnerability scanning? We have some old XP, 7 machines that control equipment that can't be upgraded/patched. I don't want to remove the vulnerability from scanning other machines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 09:34 AM
@Cole , as I mentioned below to dtracey, we are adding the vulnerabilities cause in a more comprehensive way. That, for example, will allow filtering by OS the vulnerabilities view. Another way to filter them, which you can already apply, is defining a state for those assets (e.g. EOL_asset) and creating a customize view filtering that state (using the asset state filter).
I hope this helps you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2023 11:41 AM
Hi, I must agree that Lansweeper should not show a machine as vulnerable that has been patched by a cumulative update. When will this be fixed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2023 01:27 PM
edu_ayus, well filtering thru a report is one thing, but I am more talking about excluding the asset from even being scanned which is much different. One big reason I went to the cloud was for security vulnerabilities and I hope lansweeper continues to work this part of it. Another big issue has already been mentioned is vulnerability showing up on computers that have been patched by a later update/patch that included the previous vulnerability. Thanks for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2023 09:58 PM
Is there a way to filter vulnerabilities by operating system ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 01:58 PM
Hi @dtracey ,
This is not possible yet, but it is a functionality already in our roadmap (short-term). We will provide the element/s causing a vulnerability(HW, OS, or SW) in a more explanatory way. This will allow easily filtering the vulnerabilities by OS as you are requesting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2023 01:39 PM
any update on this ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 07:01 PM
"whoami" previously suggested custom labels or additional predefined statuses. Along these lines, I would push for a free text field to note a couple of quick details like which security team member is investigating and perhaps a service ticket number from our help desk.
A strict "assign to" of an existing user could be better though as that would be easy to use as a custom filter for the CVE list.
I would also suggest being able to apply the ignore option to individual assets under each CVE as we clear them or find that is a false positive for that asset. Perhaps ignoring the CVE at the top level would mark all currently identified assets as "ignore". This way if another asset later matches on this CVE it is not overlooked. It may not be a false positive for that added asset.
Product Discussions
Share feedback, exchange ideas and find answers to Lansweeper product questions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now- Is it possible to integrate Lansweeper with Splunk? in Technical Support Solutions
- Lansweeper Connect Spring 2025: From Insights to Impact in General Discussions
- New Reboot & Review: CISA Verified Exploits — Why This One’s Worth Your Time in General Discussions
- Vulnerability on HTTP Security Header Not Detected in Product Discussions
- ISO Compliance: New Standards for 2025 in General Discussions