- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Scanning your network
- Scan Microsoft 365 targets
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
04-13-2021
08:30 PM
- edited on
11-30-2023
04:18 PM
by
Nils
![]()
This step-by-step guide explains how to scan Microsoft 365 targets with a Microsoft Cloud Services application.
With a Microsoft 365 scanning target, you can scan your Microsoft 365 data, mailbox, and ActiveSync data.
Prerequisites
- You've created a Microsoft Cloud Services application.
- You have the following Microsoft Cloud Services application information available:
- Application (client) ID
- Directory (tenant) ID
- Client secret or certificate
Add API permissions
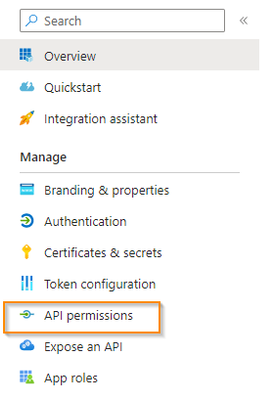
- Go to the Azure portal and navigate to App registration.
- Find the app that you've previously created.
- Go to API permissions.
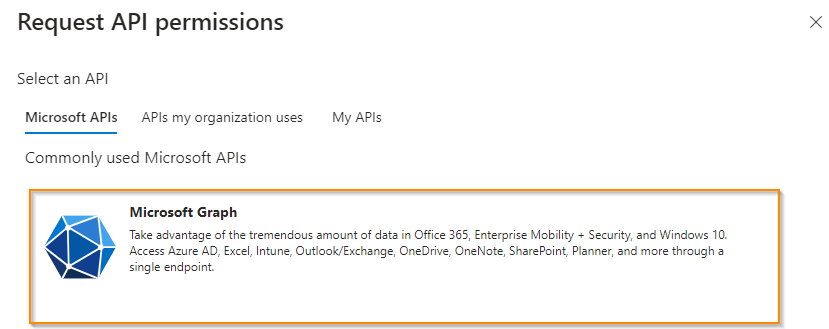
- Go to Add a permission > Microsoft Graph.
- Select Application permissions.
- Add the following API permissions:
- Directory > Directory.Read.All
- Domain > Domain.Read.All
- Group > Group.Read.All
- GroupMember > GroupMember.Read.All
- Organization > Organization.Read.All
- OrgContact > OrgContact.Read.All
- User > User.Read.All
- Select Add permissions.
- Select Grant admin consent for <organization>.
Configure PowerShell Online
To access mailbox information and ActiveSync data, enable PowerShell Online.
To enable PowerShell Online, your Lansweeper scanning server must fulfill the following prerequisites:
- Operating system: Windows 7 or newer.
- Architecture: 64-bit architecture.
- PowerShell version: 7.1.
If you only just installed this PowerShell version, reboot your machine. Your scanning server can not have pending reboots. - Scripts: To allow scripts that a trusted publisher signs, run the following command via an elevated PowerShell window on the scanning server:
Set-ExecutionPolicy RemoteSigned.
To enable PowerShell online:
- Install the latest public version of Exchange Online PowerShell by entering the following command in an elevated PowerShell terminal:
Install-Module -Name ExchangeOnlineManagement. - Go to the Azure portal and navigate to App registration.
- Locate the app you created to scan Microsoft 365.
- Copy the Application (client) ID to your clipboard.
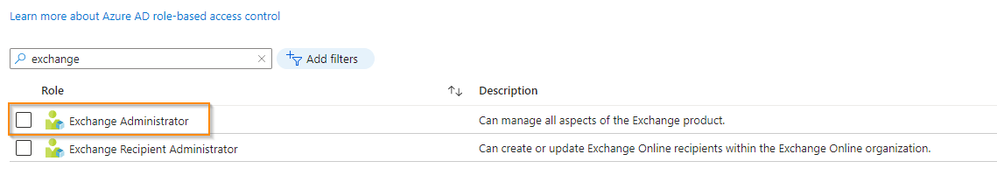
- Go to Azure Active Directory > Roles and administrators.
- Select the Exchange administrator role.
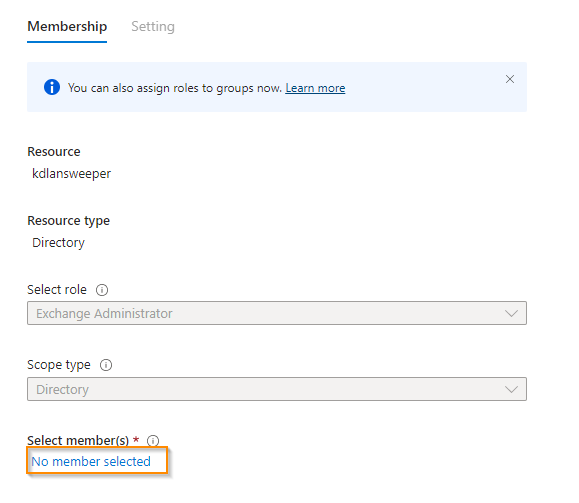
- Select Add assignments.
- Click No members selected.
- In the search bar, enter the Application (client) ID, select your app, then click Select.
- Select Next, then fill in the assignment settings and click Assign.
- Navigate back to the App registration and find the app that you created to scan Microsoft 365.
- Go to API permissions > Add a permission > APIs my organization uses > Office 365 Exchange Online.
- Select Application permissions > Exchange > Exchange.ManageAsApp > Add permissions.
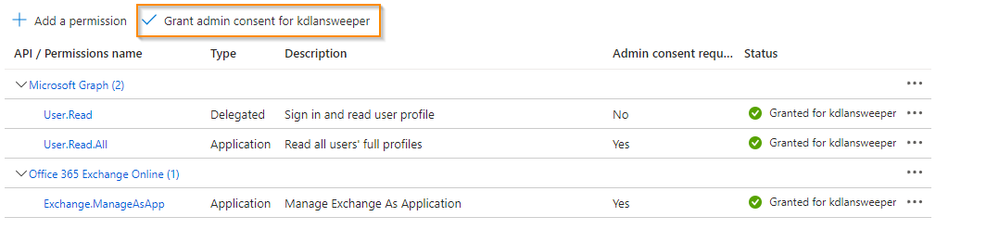
- Select Grant admin consent for <organization>.
Configure Lansweeper to scan Microsoft 365
- In the web console, go to Scanning > Scanning Credentials.
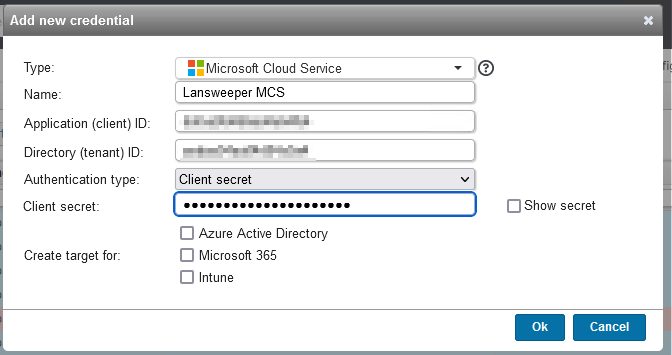
- Select Add new credential.
- Fill in the following fields:
- Type: Microsoft Cloud Service
- Name: Name of your application
- Application (client) ID: Copy from Azure portal > App registration > <your application> > Overview
- Directory (tenant) ID: Copy from Azure portal > App registration > <your application> > Overview
- Authentication type: Select either:
- Client secret: Copy from Azure portal > App registration > <your application> Certificates & secrets > Secret ID
- Certificate thumbprint: Copy from Azure portal > App registration > <your application> Certificates & secrets > Thumbprint
To scan mailbox and ActiveSync information using PowerShell you must use the certificate thumbprint authentication type.
- Select Microsoft 365 then Ok.
Lansweeper can now scan your Microsoft 365 targets.
Was this post helpful? Select Yes or No below!
Did you have a similar issue and a different solution? Or did you not find the information you needed? Create a post in our Community Forum for your fellow IT Heroes!
More questions? Browse our Quick Tech Solutions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now