- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Sites
- Configure Microsoft Entra ID (Azure AD) with Lansw...
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This documentation is for the old UI. For documentation for the new preview UI, Knowledge Base - Preview UI.
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
11-28-2021
07:30 PM
- edited
a month ago
by
Nils
![]()
This page provides a step-by-step guide on configuring Microsoft Entra ID (Azure AD) to set up Single Sign-On (SSO) for Lansweeper Sites.
There are two main ways to log into Lansweeper Sites: using a login/password created in Sites itself or using SSO. Logging in with SSO is supported for identity providers that offer SAML (Security Assertion Markup Language) or OIDC (OpenID Connect). Azure Active Directory is such an identity provider or IdP.
This article explains how to do the necessary SSO setup in Microsoft Entra ID (Azure AD) to then complete an SSO configuration in Lansweeper Sites. Note that for these Microsoft Entra ID (Azure AD) instructions we're using SAML as an SSO connection type.
Create an application in Microsoft Entra ID (Azure AD)
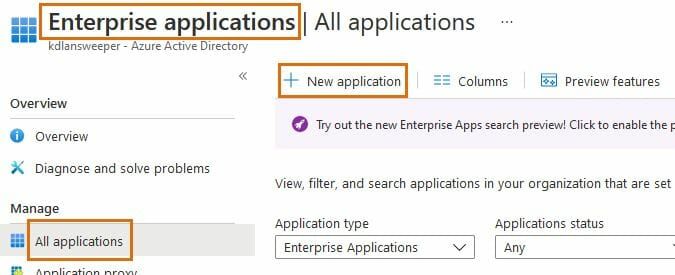
- Log into the Azure portal and browse to the Azure Active Directory resource.
- Go to the Enterprise applications menu and select New application.
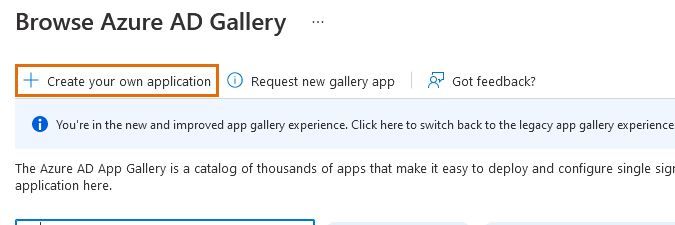
- Select Create your own application.
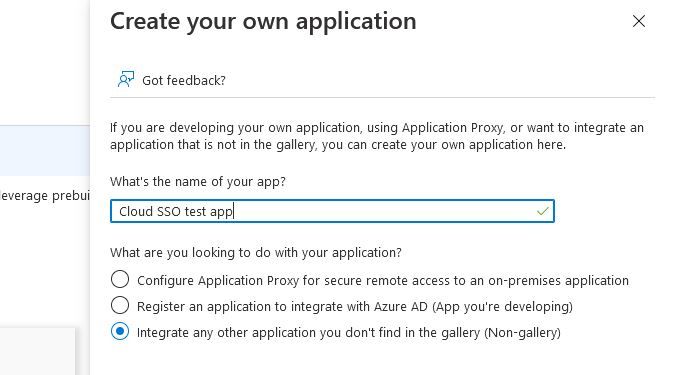
- In the resulting pop-up, enter a descriptive name for your application and select Integrate any other application you don't find in the gallery (Non-Gallery).
- Finally, select Create.
Configure your SSO app
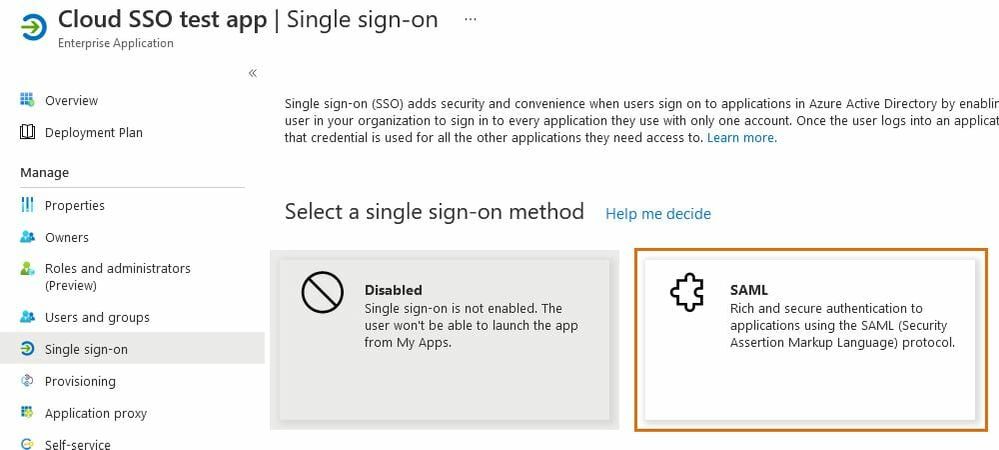
- In the Single sign-on menu of your newly created app, select SAML.
- Copy the Entity ID from the Add SSO Connection pop-up in Lansweeper and paste it in your SAML settings.
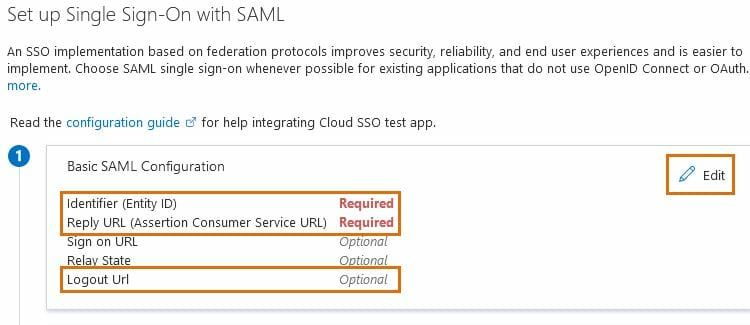
- Select Edit under Basic SAML Configuration.
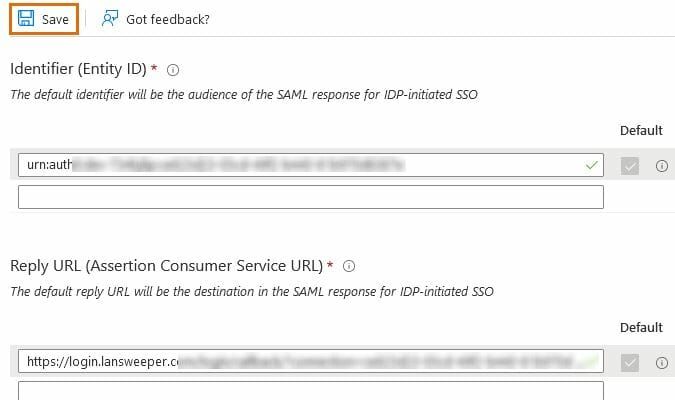
- Enter the Entity ID into the Identifier (Entity ID) field and set the new ID as default.
- Copy the Assertion Consumer Service (ACS) URL from the Add SSO Connection pop-up in Lansweeper and paste it into the Reply URL (Assertion Consumer Service URL) field.
- Copy the SingleLogout Service (SLO) URL from the Add SSO Connection pop-up in Lansweeper and paste it into the Logout Url field.
- Select Save.
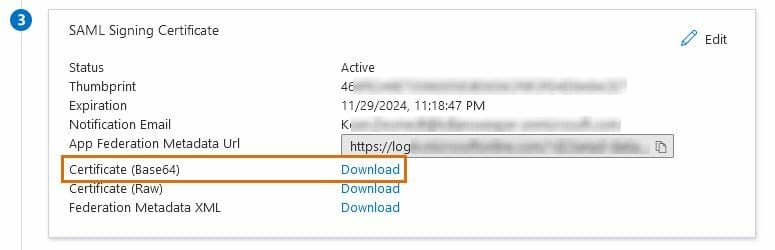
- In the SAML Signing Certificate section of your app's SSO config, download the Base64 certificate. Upload it in the Add SSO Connection pop-up in Lansweeper.
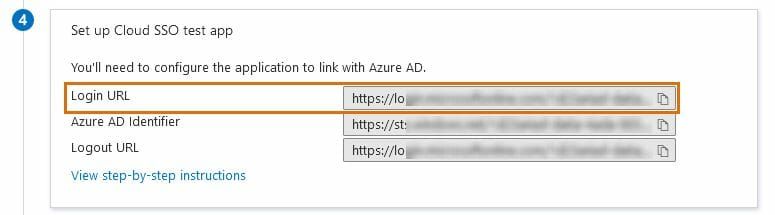
- In the Set up <Your App Name> section of your app's SSO config, copy the Login URL.
- Paste it into the Add SSO Connection pop-up in Lansweeper. The field you need to paste the value into in Lansweeper is called Sign in URL. Optionally, you can also copy the Logout URL from Microsoft Entra ID (Azure AD) to Lansweeper.
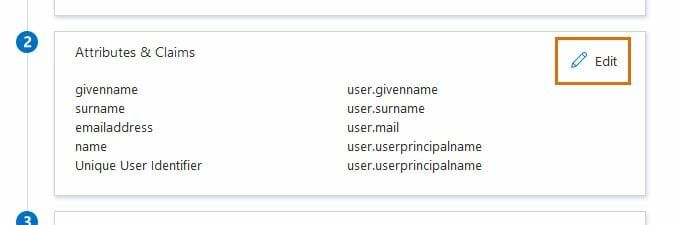
- In the Attributes & Claims section of your app's SSO config, select Edit.
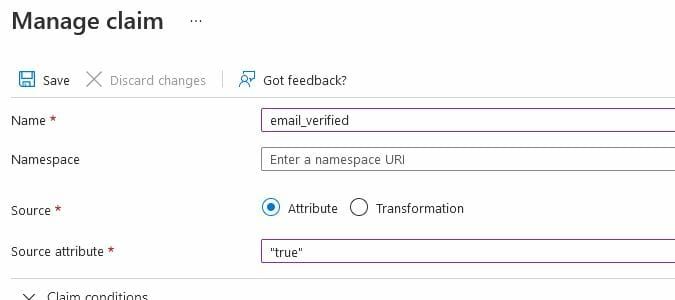
- Choose Add new claim, configure the new claim as mentioned below and select Save.
For the source attribute, entertrueand select it. Your submission will automatically be surrounded by quotes.- Name:
email_verified - Source: Attribute
- Source attribute:
true
Do not skip this step. Adding this attribute is important as it is required by Lansweeper Sites' underlying SSO login process. - Name:
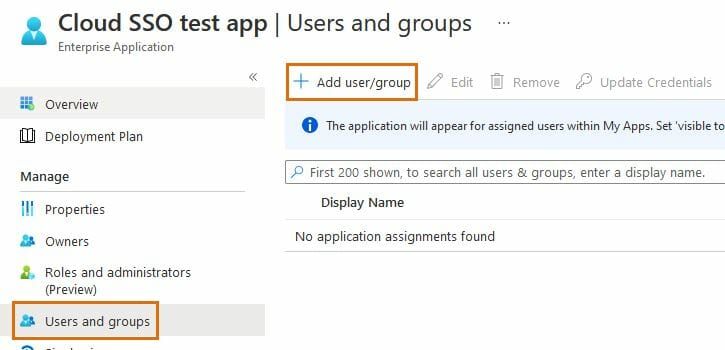
- In the Users and groups menu of your app, select Add user/group.
- Select the users and/or groups that will be able to log into Sites using SSO. As an Microsoft Entra ID (Azure AD) admin, you will be able to monitor your users' SSO logins in Microsoft Entra ID (Azure AD).
Was this post helpful? Select Yes or No below!
Did you have a similar issue and a different solution? Or did you not find the information you needed? Create a post in our Community Forum for your fellow IT Heroes!
More questions? Browse our Quick Tech Solutions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now