- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Cyber Security and Risk Insights
- Understanding exploitability fields
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This documentation is for the old UI. For documentation for the new preview UI, Knowledge Base - Preview UI.
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 10-30-2024 04:42 PM
This page provides more information on the various fields in Lansweeper Sites used to assess the exploitability of a vulnerability.
Exploitability refers to how easily an attacker can take advantage of a vulnerability. Understanding exploitability is crucial for developing effective mitigation plans based on vulnerability information.
For more information on vulnerability risk assessment in general, head over to Introduction to Vulnerability Risk Assessment.
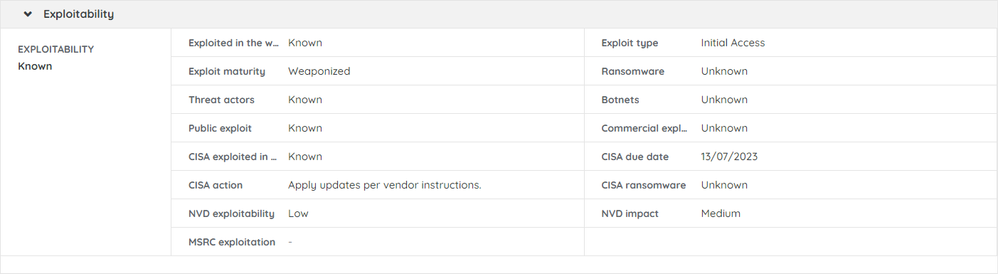
Lansweeper provides information from several sources to evaluate the exploitability of each vulnerability. This results in an aggregated value, referred to as the exploitability. The easiest way to find the exploitability of a vulnerability is to navigate to Risk Insights > Active vulnerabilities, and selecting the vulnerability you'd like to inspect.
More detailed information is also available from each specific source, which we'll dive into.
Exploitability fields
Lansweeper provides information from four main sources: CISA, MSRC, NVD, and VulnCheck.
CISA (Cybersecurity and Infrastructure Agency)
- Exploited in the wild: Indicates whether CISA has detected an exploit using this vulnerability.
- Action: Recommended actions users should take to mitigate the exploit.
- Due date: The deadline for applying a patch or mitigation.
- Ransomware: Information on whether the vulnerability has been used in ransomware campaigns.
MSRC (Microsoft Security Response Center)
- Exploitability: Indicates the likelihood of an exploit using this vulnerability, categorized as exploitation detected, more likely, less likely, or unlikely, based on Microsoft's observations.
NVD (National Vulnerability Database)
- Exploitability: A score indicating how difficult it is for an attacker to exploit the vulnerability, rated as low, medium, high, or critical.
- Impact: Provides details on the potential impact of the vulnerability on systems.
VulnCheck
- EPSS score: The Exploit Prediction Scoring System (EPSS) predicts the likelihood of a vulnerability being exploited in the wild within the next 30 days. It assigns a score between 0 and 1 (or 0 to 100%), with higher scores indicating a greater probability of exploitation.
The EPSS score consists of:- EPSS score: Indicates how likely a vulnerability is to be exploited.
- EPSS percentile: Displays the percentile rank of the vulnerability compared to all others in the EPSS dataset.
- Last modified: Records the last time the EPSS data for this particular vulnerability was updated.
Many organizations rely on EPSS to prioritize their vulnerability management efforts. A high-scoring vulnerability may warrant immediate action, while lower scores may allow for deferring or handling vulnerabilities through other means. - Exploit type classification: Categorizes exploits based on their potential impact, distinguishing between higher and lower-risk exploits.
Possible classifications include: Initial access, Remote with credentials exploits, Local, Client-side, Infoleak, and Denial of Service. - Max exploit maturity: Describes the development stage of existing exploit techniques and the availability of exploit code.
Possible maturity levels include: - Weaponized: Refers to explicitly malicious exploits (e.g. integrated into malware) that have been reported as exploited in the wild. These exploits are often used in real-world attacks, work reliably across many targets (e.g. exploits in MetaSploit, VulnCheck IAI, CANVAS, or Core Impact), and may include secondary payloads like droppers or implants.
- Proof of Concept (POC): Demonstrates the potential for exploitation, but is not yet weaponized. POCs may come in various forms, such as blog posts, Python scripts, or curl commands.
- Reported exploited: Indicates confirmed reports of a vulnerability being exploited in the wild. This includes references from various sources like threat actor indexes, ransomware databases, botnets.
- Public exploit found: Indicates whether a publicly available exploit code or method for the vulnerability has been identified.
- Commercial exploit found: Indicates whether exploit code or methods for the vulnerability are available through commercial vendors.
- Reported exploited by threat actors: Documents instances where malicious threat actors actively exploited the vulnerability.
- Reported exploited by ransomware: Documents instances where ransomware groups exploited the vulnerability in their attacks.
- Reported exploited by botnets: Documents instances botnets have used the vulnerability to compromise systems.
- Historical exploitation data: Provides a timeline of past exploitation events, showing the history of the vulnerability's use in attacks.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now