- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Requirements
- Configure Windows Firewall for agentless scanning ...
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
11-14-2012
07:30 PM
- edited on
07-17-2024
03:31 PM
by
Nils
![]()
This article offers guidance on configuring Windows Firewall to allow WMI traffic, enabling remote scanning of Windows computers, and provides step-by-step instructions using the group policy editor or command prompt.
Lansweeper pulls Windows computer data from WMI (Windows Management Instrumentation), a management infrastructure built into Windows operating systems. The initial connection to a client machine is made over TCP port 135. By default, Windows then sends the WMI data over random ports in the 1025-5000 or 49152-65535 range.
Lansweeper first performs broadcasts to identify the Windows devices in your network. Next, discovered devices are added to a queue for further processing. Lansweeper then directly scans the Windows devices to gather detailed data, which involves sending a new WMI request to each device.
In order to remotely scan Windows computers, you must ensure that the machines' firewalls are properly configured to allow all WMI traffic. Simply opening specific ports is not enough, as traffic is sent over random ports in the 1025-5000 or 49152-65535 range. For more information, see Ports scanned or used by Lansweeper.
This article specifically explains how to configure Windows Firewall, also known as Windows Defender Firewall, for remote scanning of Windows computers. Windows Firewall has a remote administration setting you can enable to allow WMI traffic. The easiest way to enable this setting for all of your domain computers is using group policies.
Configuring Windows Firewall visually
To configure Windows Firewall on your client machines to allow WMI traffic:
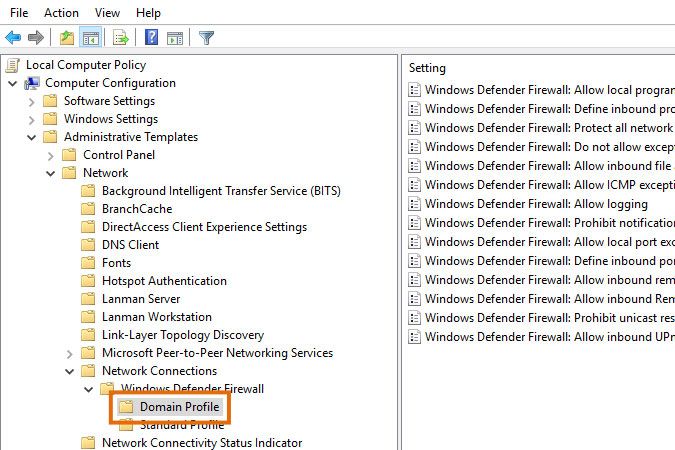
- Open the group policy editor for your client machines.
- Browse to one of the sections listed below. Which one you have depends on your OS.
Computer Configuration\Administrative Templates\Network\Network Connections
\Windows Defender Firewall\Domain ProfileorComputer Configuration\Administrative Templates\Network\Network Connections
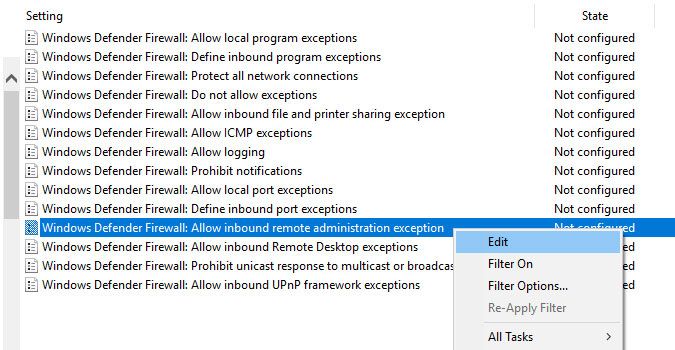
\Windows Firewall\Domain Profile - Right-click one of the settings listed below and choose Edit. Which one you have depends on your OS.
- Windows Defender Firewall: Allow inbound remote administration exception
- Windows Firewall: Allow inbound remote administration exception
- Windows Firewall: Allow remote administration exception
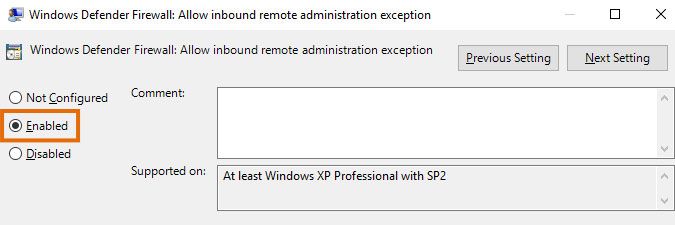
- Select the Enabled option to enable the group policy.
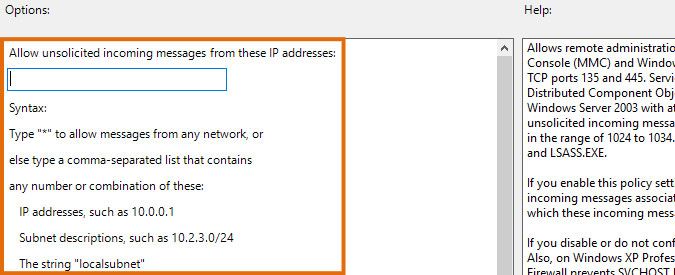
- In the options under Allow unsolicited incoming messages from these IP addresses, enter your Lansweeper scanning server's IP address and continue. Alternatively, submit the "*" wildcard to allow traffic from all IP addresses.
- Wait for your policy to take effect on your client machines, which may take several hours. Alternatively, run the below command on your machines to force the group policy to apply.
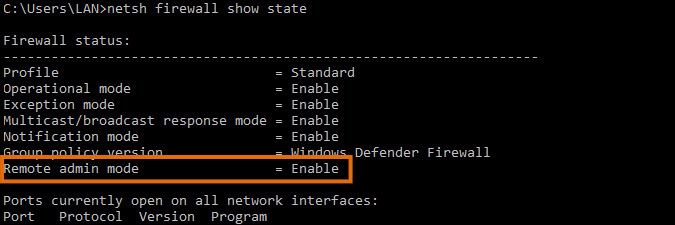
gpupdate /force - Verify whether your policy is correctly applied. You can do this by running the below command on a machine.
netsh firewall show state
Configuring Windows Firewall through commands or scripts
If you prefer to configure Windows Firewall through commands or scripts, you can either:
- Run the commands below in an elevated command prompt on the client machine. These commands will run successfully on both older and newer operating systems. They may generate deprecation warnings on newer operating systems but will function regardless.
call netsh firewall set service RemoteAdmin enablecall netsh firewall add portopening protocol=tcp port=135 name=DCOM_TCP135 - Download and run this script in an elevated Command Prompt on the client machine. This ensures that DCOM, Windows Firewall and other settings are correct. You can open the script in a text editor to review its contents, before executing in command prompt.
Was this post helpful? Select Yes or No below!
Did you have a similar issue and a different solution? Or did you not find the information you needed? Create a post in our Community Forum for your fellow IT Heroes!
More questions? Browse our Quick Tech Solutions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now