- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Scanning your network
- Scan Microsoft Entra ID (Azure AD) users and group...
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
03-30-2022
08:30 PM
- edited on
12-14-2023
09:08 PM
by
sophie
![]()
Lansweeper is capable of scanning Microsoft Entra ID (Azure Active Directory) users and groups using a scanning target. This scanning target makes use of the Microsoft Cloud Service credential type, which can also be used to scan your Intune assets or Microsoft 365 tenant. This credential makes use of Modern Authentication and the Microsoft Graph API, using application permissions.
Prerequisites
To scan your Microsoft Entra ID (Azure AD) make sure that:
- You've already set up your Microsoft Cloud Services application.
- You're in possession of your Microsoft Cloud Services application's Application (client) ID, Directory (tenant) ID, and Client secret or certificate. These are obtained when creating the application.
Add permissions to the Microsoft Graph application
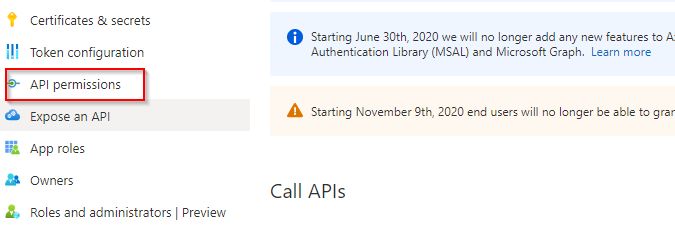
- Open your company's Azure portal and go to App registrations.
- Select the the app you've already created, then select the API permissions tab.
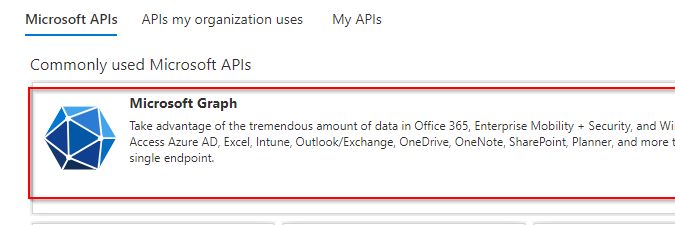
- Select Add permission then select Microsoft Graph from the API list.
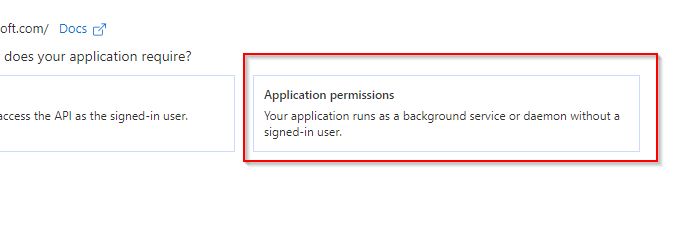
- As you're setting up the Microsoft Graph API to enforce modern authentication, you will need to add Application permissions. Select Application permissions.
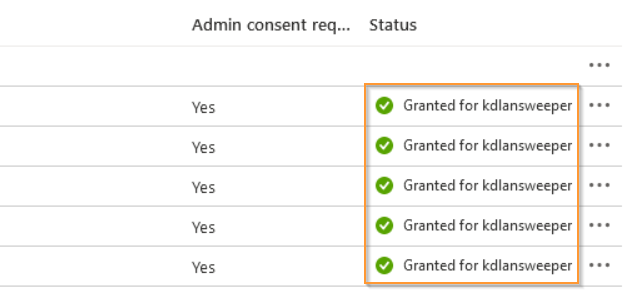
- Add the Group.Read.All, GroupMember.Read.All and User.Read.All API permissions. These are required to be able to scan all Microsoft Entra ID (Azure Active Directory) data. Once the permissions are added, select Save button and double-check the permissions listed.
- Select Grant admin consent for <organization> and select Grant in the resulting pop-up. The added permissions should now show Granted for <organization>.
Add a Microsoft Cloud Service credential
- In Lansweeper, navigate to Scanning > Scanning Credentials.
- Select Add New Credential.
- In the Type dropdown, select Microsoft Cloud Service.
- Enter a name for your credential.
- Enter the Application ID and Directory ID that were created when you created a Microsoft Cloud Services application.
- For Authentication type, select either Client secret or Certificate thumbprint.
- Enter the client secret or certificate thumbprint that was created when you created a Microsoft Cloud Services application.
- If you'd like a Microsoft Entra ID scan target to be automatically created, select Microsoft Entra ID (Azure Active Directory). If you plan to use the same credentials for multiple scan targets, you can select those as well.
- Select OK.
If you're using the Microsoft Cloud Service credential for multiple scan targets, ensure that the app has sufficient API permissions to scan the selected scanning targets. If you'd like to use the credential for both Microsoft 365 and Microsoft Entra ID (Azure Active Directory) scanning for example, make sure application permissions are set for both.
If you already have a Microsoft Cloud Services credential, you can add a new Microsoft Entra ID (Azure Active Directory) Scanning target to it via Scanning > Scanning Targets. During the creation of your Microsoft Entra ID (Azure Active Directory) scanning target, you can select a pre-existing credential.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now