- Lansweeper Community
- Forums
- Product Discussions
- Re: Addressing NVD Insufficient Data - Impact on V...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 10:53 AM - edited 05-27-2024 03:30 PM
** Update 27th May 2024**
We are pleased to announce that our integration with VulnCheck, our new primary vulnerability intelligence data provider, is now complete. Customers can now test and utilize the updated vulnerability data.
Our initial release focuses on critical and high-risk vulnerabilities that may exist in your environment. Over the coming weeks, we will expand coverage to include additional lower-risk vulnerabilities, with continuous improvements expected over time.
** Update 17th April 2024**
Lansweeper engineering has established a targeted completion date, set for June. We'll continue to keep you informed as we make progress.
** Update 5th April 2024**
Lansweeper has selected VulnCheck (https://www.vulncheck.com) to become our primary partner when it comes to vulnerability intelligence data. We are in the process of planning the integration and will update shortly on the expected timescales.
What is the problem?
Recently, Lansweeper has learned that the National Vulnerability Database (NVD), provided by the National Institute for Standards and Technology (NIST), has temporarily stopped analyzing most new vulnerabilities. From their website:
Many organizations, including Lansweeper, have relied on the NVD to assist with vulnerability and risk management for nearly two decades. It For us, it contains the specific metadata needed to associate published vulnerabilities with specific products and systems in an IT environment.
While the above notice appeared on February 15th, it was not evident that the delay would be so impactful, particularly because NVD has offered no additional communication.
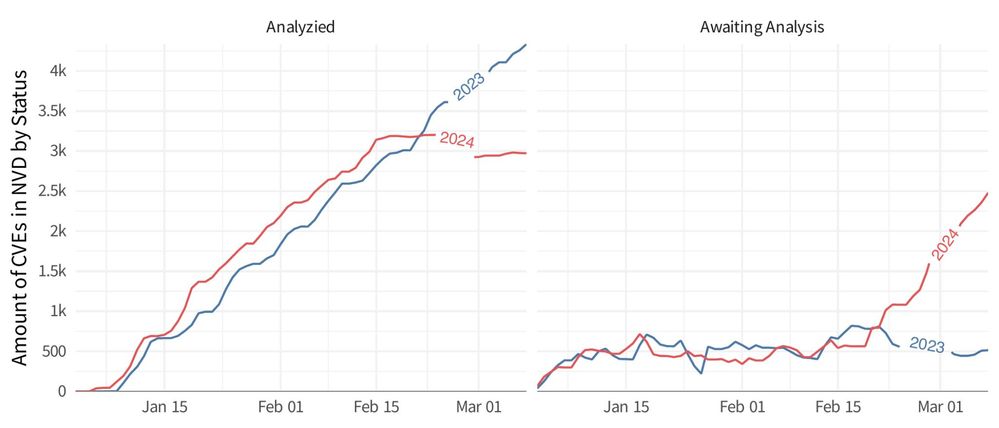
However, per this blog from Resilient Cyber, you can see for yourself how the data analyzed by NVD has dropped off considerably since that date:
While this delay is an industry-wide issue, we are unable to procure a firm resolution date from NIST at this time.
The result is that Lansweeper has insufficient data from NVD to identify most vulnerabilities in your environment since February 15th.
What are we going to do about it?
To rectify this issue, Lansweeper is designing a new method of providing this vital information to our customers and has prioritized an engineering fix to resolve this issue.
What can you do in the meantime?
In the meantime, vulnerabilities prior to February 15th are not impacted. Similarly, our zero-day vulnerability and Patch Tuesday reports are available too.
Thank you for your patience while we make this transition, and we’ll keep you up to date as we make progress over the coming weeks.
Best regards,
Maria Orellana
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2024 02:14 PM
If I look at the list I see only old CVE's how should i be able to see if it is working now?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2024 03:20 PM
Only critical and high-risk vulnerabilities are targeted in the initial release; lower-risk vulnerabilities are not yet included
~~~~~~~ (〃 ̄︶ ̄)人( ̄︶ ̄〃) ~~~~~~~
Sweep that LAN, sweep it!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2024 04:44 PM - edited 05-30-2024 05:49 PM
Thank you, David, for the update. Please confirm if the fix is rolled for all OS (Linux, Windows, Mac).
Also, do you have a date for covering lower-risk CVEs for our internal tracking purposes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2024 02:39 PM
Critical and high-risk vulnerabilities are included for all asset types (Windows, Linux, Mac). lower-risks CVEs will be included in the coming weeks.
~~~~~~~ (〃 ̄︶ ̄)人( ̄︶ ̄〃) ~~~~~~~
Sweep that LAN, sweep it!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2024 10:17 AM
Can we get an update on this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 10:16 AM - edited 04-22-2024 10:30 AM
Hello,
Thank you for the announcement. We have been told that the rollout planned in Jun'24 addresses the observation mentioned below. Please confirm if the rollout will fix the observation shared below.
Note: This is just a sample, however, we found a host is reported with 800+ CVEs, but all of the applicable patches shared by the OS vendor are already applied and the host is clean. There is a huge discrepancy in the findings by Lansweeper.
Observation: Minor versions released by OS vendors (RHEL/CentOS) are not considered for vulnerability detection.
- Sample CVE: CVE-2016-4448
- Affected Component: Libxml2
- OS Platform: CentOS7
- Patch released by vendor: libxml2-2.9.1-6.el7_2.3 9 (RHSA-2016:1292 - Security Advisory - Red Hat Customer Portal
- Expected version by Lansweeper: 2.9.4 & Above
- Installed version on the host: libxml2-2.9.1-6.el7_2.3 9
- Is the host vulnerable with CVE: Yes (as per Lansweeper), No (as per the patch applied)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 12:32 PM
Hi @saikumark,
Thanks for reaching out.
Yes, I can confirm that the expected rollout date for the NVD replacement is 24 June.
Regarding the case you mention, I would suggest you open a support case so that we can track all the information you give us. At first glance, I don't see the connection between the case and the NVD replacement. It could be a normalization or false positive issue. Let's get the team working on this.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 03:31 PM
Hi @saikumark,
I'm reviewing the answer the support team gave you after their research and it seems to be related to the NVD delays. Even though the CVE is from 2016, "This vulnerability has changed since it was last analysed by NVD. It is awaiting reanalysis which may result in further changes to the information provided".
So again, the discrepancy in this case is due to NVD delays.
Thank you very much!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 02:44 PM
Thank you, for the confirmation. We have already opened a case with the support and we have been told that the reported issue is due to a data issue with NVD.
Product Discussions
Share feedback, exchange ideas and find answers to Lansweeper product questions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now- Discover the Power of Lansweeper's Integration with TOPdesk! in General Discussions
- Addressing NVD Insufficient Data - Impact on Vulnerability Assessments in Lansweeper in Product Discussions
- Vulnerabilities Risk Assessment sql query in Product Discussions
- Known Issue > Vulnerability Risk Assessment - Performance Issues for Microsoft cumulative patching in General Discussions
- Vulnerability Risk Assessment - Performance Issues for Microsoft cumulative patching in Product Discussions