We recently had a customer reaching out to our support to assist setting up Digitally signed emails in the Lansweeper Helpdesk.
What?
This blog describes how first, to create a self-signed certificate, secondly, how to configure Outlook to send Digitally signed emails using this certificate.
Phase 1: Generate a Self-Signed certificate
Generate your own Certificate Authority (CA)
This will create a new Certificate Authority. If you have done this step before, you can skip this step.
openssl req -nodes -new -x509 -days 3650 -newkey rsa:4096 -keyout ca.key -out ca.crt -extensions v3_ca -subj "/CN=My-CA"
Generate a key and signing request (*.key and *.csr)
This will generate a new private key and a certificate signing request (CSR) for a specific user. You will be prompted for some additional information. You need to enter the email address here, most other info can be default.
openssl req -nodes -new -newkey rsa:4096 -keyout smime_test_user.key -out smime_test_user.csr
Generating a RSA private key
............................................................................................................................................++++
........................................................................................................................................................................................................................++++
writing new private key to 'smime_test_user.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:BE
State or Province Name (full name) []:
Locality Name (eg, city) [Default City]:
Organization Name (eg, company) [Default Company Ltd]: <ENTER YOUR ORGANIZATION NAME HERE>
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []: <ENTER YOUR HOSTNAME HERE>
Email Address []: <ENTER YOUR EMAIL ADDRESS HERE>
Sign the request with the CA from step 1
openssl x509 -req -days 3650 -in smime_test_user.csr -CA ca.crt -CAkey ca.key -set_serial 1 -out smime_test_user.crt -addtrust emailProtection -addreject clientAuth -addreject serverAuth -trustout -extensions smime
Signature ok
subject=C = BE, ST = Some-State, O = Internet Widgits Pty Ltd, CN = <YOUR CN>, emailAddress = <YOUR EMAIL ADDRESS>
Getting CA Private Key
Package the key and certificate into a pkcs12 format
You will be asked to supply a password which will be used to encrypt the resulting file (.p12 file).
openssl pkcs12 -export -in smime_test_user.crt -inkey smime_test_user.key -out smime_test_user.p12
Enter Export Password:
Verifying - Enter Export Password:
Copy the certificates to your target Windows machine
You’ll need to copy the ca.crt and smime_test_user.p12 files to the machine from where you will be sending email.
Phase 2: Configure Outlook
Copy ca.crt and smime_test_user.p12 to the Windows machine
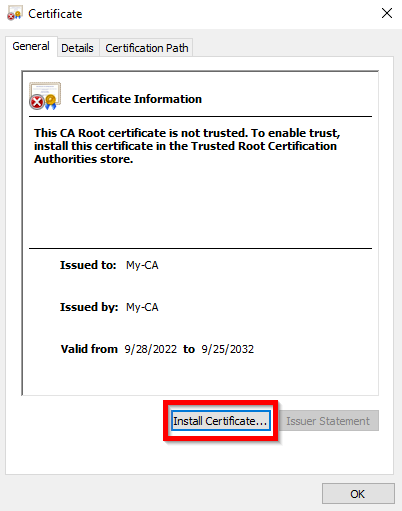
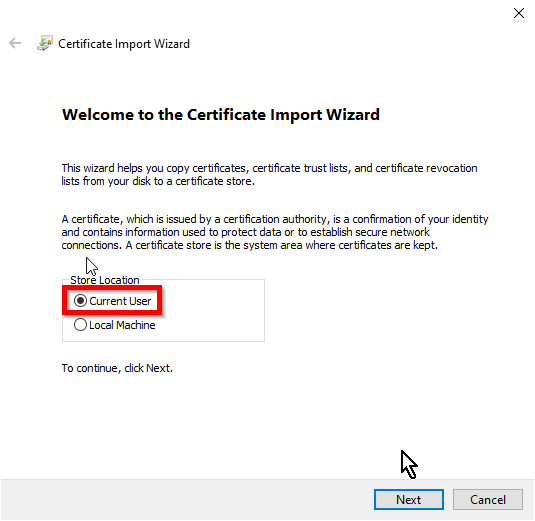
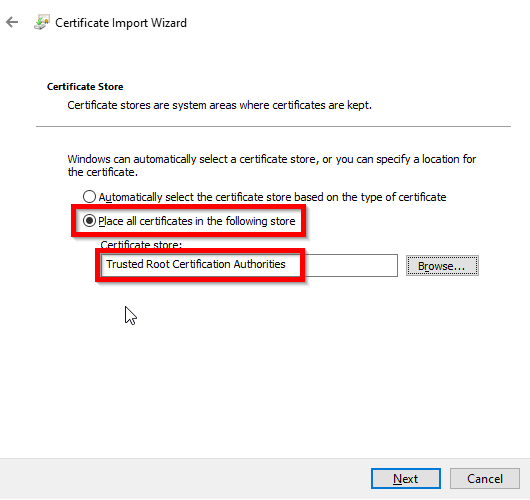
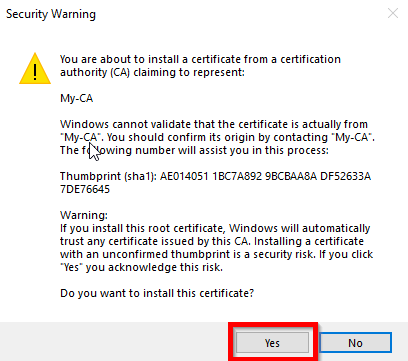
Install the root CA on the user's Windows machine
Double click on the ca.crt file
Install the smime_test_user.p12 certificate&key in Outlook
Go to Outlook options, then Trust Center Settings.

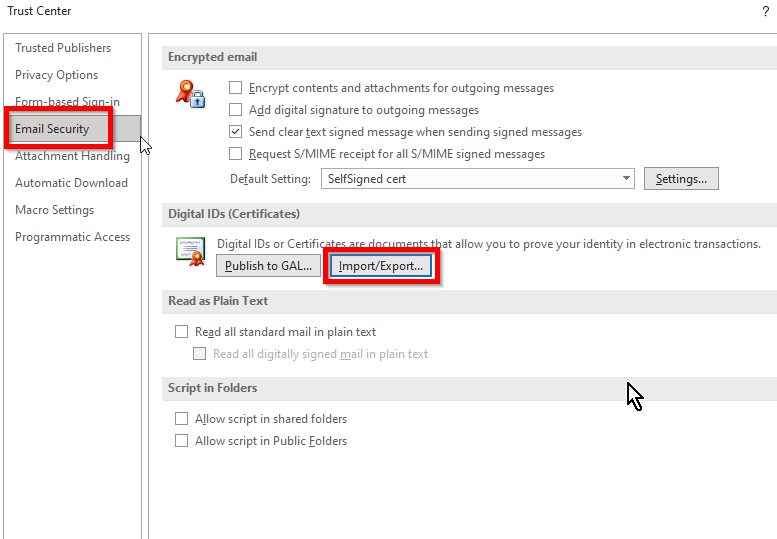
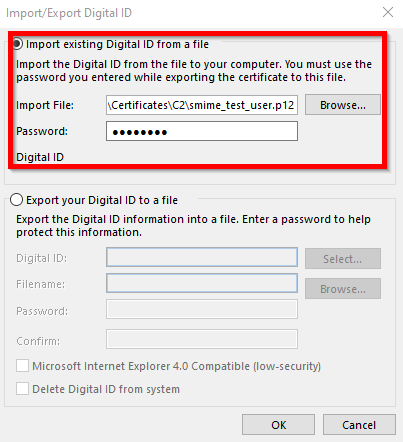
Import the smime_test_user.p12 file here. You need to supply the password you used when creating the p12 file.
Go to Encrypted email Settings…
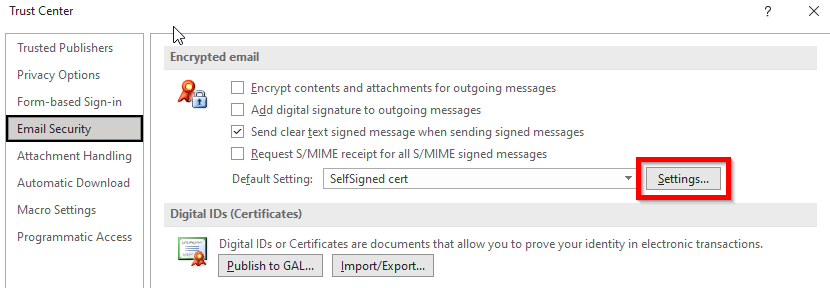
And Choose… your certificate. You need to give a Security Settings Name too (any name):
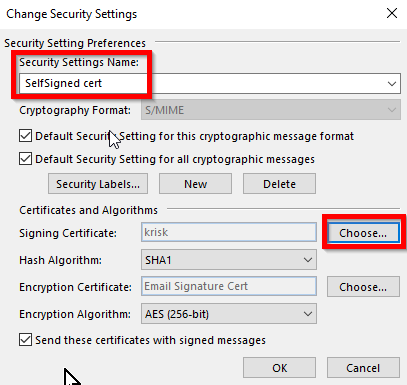
Phase 3: Now you can send a signed email!
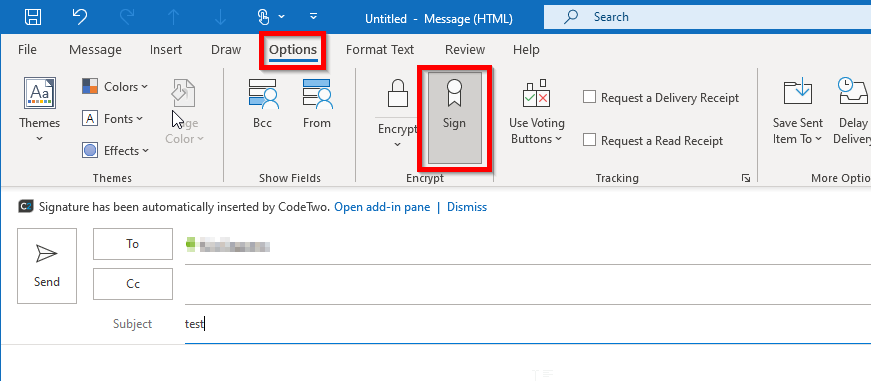
Create a new, email, then go to Options and enable “Sign”
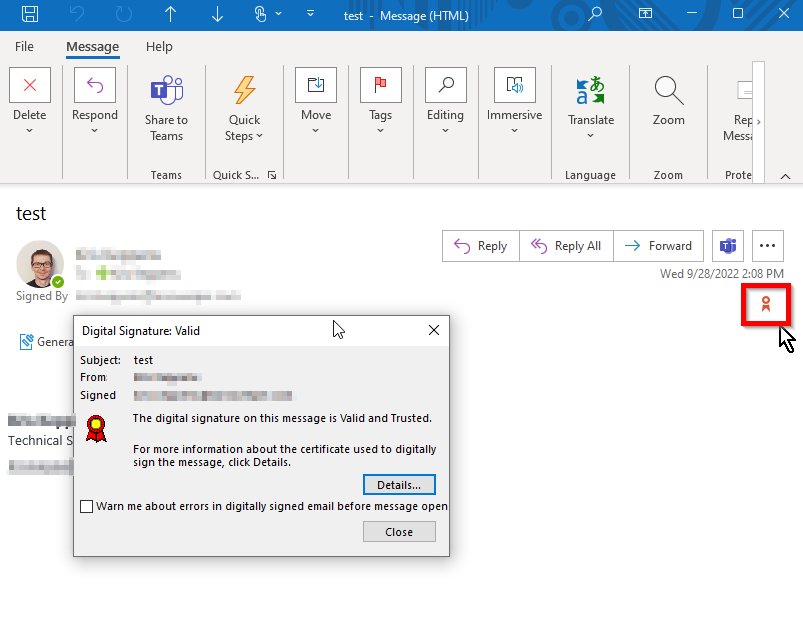
On the receiving end, you will notice the certificate icon on the email.
| Note: |
|
Since it is a self-signed certificate, the receiver will have to explicitly “Trust” the certificate or install the ca.crt too.
|
