- Lansweeper Community
- Forums
- General Discussions
- Re: LanSweeper Scan causes failed logon event logs...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2022 05:13 PM - last edited on 04-02-2024 10:11 AM by Mercedes_O
Hi all,
since some time (i don't know exactly since when - maybe since the update to v10.2.4.0) LanSweeper is spamming failed logon events (4625) in our security event logs on all our domain controllers.
here is an example event (removed IPs / hostnames)
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}" />
<EventID>4625</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12544</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2022-11-22T15:16:54.207895700Z" />
<EventRecordID>453580707</EventRecordID>
<Correlation />
<Execution ProcessID="720" ThreadID="6748" />
<Channel>Security</Channel>
<Computer>...</Computer>
<Security />
</System>
<EventData>
<Data Name="SubjectUserSid">S-1-5-18</Data>
<Data Name="SubjectUserName">...</Data>
<Data Name="SubjectDomainName">...</Data>
<Data Name="SubjectLogonId">0x3e7</Data>
<Data Name="TargetUserSid">S-1-0-0</Data>
<Data Name="TargetUserName" />
<Data Name="TargetDomainName" />
<Data Name="Status">0xc000006d</Data>
<Data Name="FailureReason">%%2313</Data>
<Data Name="SubStatus">0xc0000064</Data>
<Data Name="LogonType">3</Data>
<Data Name="LogonProcessName">Schannel</Data>
<Data Name="AuthenticationPackageName">Kerberos</Data>
<Data Name="WorkstationName">...</Data>
<Data Name="TransmittedServices">-</Data>
<Data Name="LmPackageName">-</Data>
<Data Name="KeyLength">0</Data>
<Data Name="ProcessId">0x2d0</Data>
<Data Name="ProcessName">C:\Windows\System32\lsass.exe</Data>
<Data Name="IpAddress">...</Data>
<Data Name="IpPort">58937</Data>
</EventData>
</Event>
It looks like that this event comes up for every asset scan which was performed and it's always the same status "unknown username or password" for target user SID "S-1-0-0"
I already checked all of our windows credentials and the mapping in LanSweeper but they are fine and didn't changed at all (and also working for auditing our windows assets)
I think there is something else going wrong because of the strange target user SID.
Maybe someone know how to stop or fix these logon attamps from the LanSweeper scanning service or had the same issue?
Thanks a lot and kind Regards,
Stephan
- Labels:
-
Scanning
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2023 09:12 AM
Hi Stephan,
I see the same behaviour on my DCs after switching over to LDAPS. Did you ever find a solution for it?
Additionally I can log these failed Kerberos authentication attempts from the Lansweeper server, which are showing a bit before the event you posted. You can see here, that an authentication attempt is made with the account name: "host" , looks like a broken variable to me. Of course this authentication attempt results in a user unknown response.
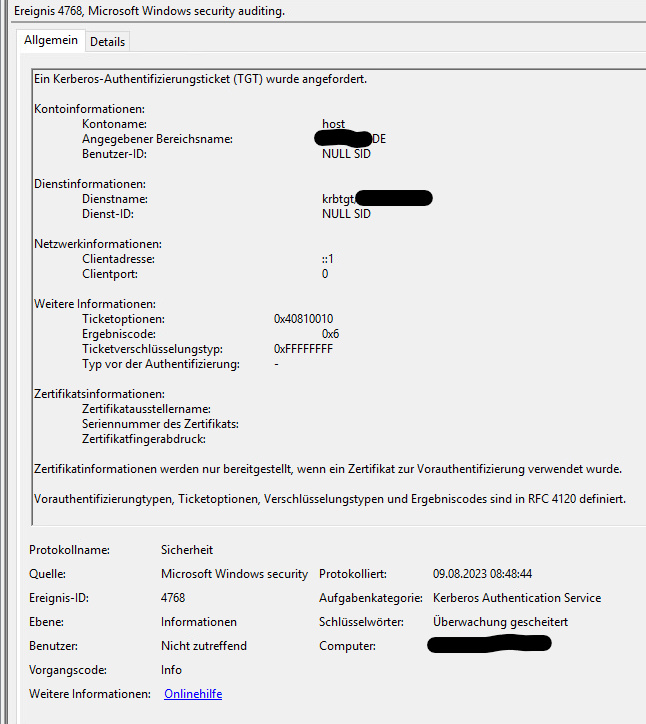
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2023 11:00 AM
Hi Martin,
unfortunately I still have no solution for this issue, even the lansweeper support couldn't fix it after some troubleshooting. My support ticket was closed because it wasn't reproducable in the lab.
I still use lansweeper with a LDAP (non-secure) connection to workaround this issue.
Regards,
Stephan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2022 10:00 AM
update: I contacted the lansweeper support and they figured out that the usage of LDAPS was the issue. Switching back to LDAP instead of LDAPS (in Scanning -> Scanning targets -> On-Premises Active Directory Scanning Options -> LDAP(S) ) fixed the issue for now.
They currently try to reproduce this issue on a lab to provide a fix
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2023 08:20 PM
Stephan_R, I wonder if this was recently fixed with the update of 10.4.1.0.
Lansweeper Changelog - Lansweeper.com
There's something similar listed there as LAN-14431. Try upgrading to this version and see if that helps you out.
Please keep us posted how it goes.
Lansweeper Employee
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 12:32 PM
Hi Tim_N, thank you for the hint.
I've updated and tested with LDAPS again right now, but unfortunately I still have the same issue.
Kind Regards,
Stephan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2023 10:53 AM
@Stephan_R, if the issue isn't fixed after upgrading, I would recommend reaching out to our support team again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 04:12 PM - edited 02-06-2023 04:12 PM
the issue couln't be reproduced in the test lab from Lansweeper support.
So this issue still persists in my environment, as soon as I endable LDAPS in LanSweeper
Any hints for troubleshooting or a Workaround (except switch to LDAP non-secure 😉 ) is welcome
Kind Regards,
Stephan
General Discussions
Find answers to technical questions about Lansweeper.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now- Lansweeper Tips & Tricks – February 2026 in General Discussions
- Lansweeper Open Office Hours - February 26, 2026 in General Discussions
- How can I prevent Lansweeper from creating duplicate assets? in Technical Support Solutions
- How do I force Lansweeper to use a different scan protocol for certain devices? in Technical Support Solutions
- What is the process for manually importing assets? in Technical Support Solutions
