- Lansweeper Community
- Forums
- Product Discussions
- Want to know the vulnerabilities affecting an asse...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 11:38 AM - last edited on 06-14-2023 08:06 PM by Mercedes_O
Hi,
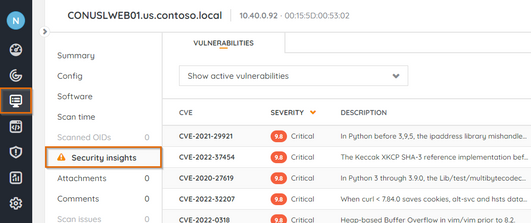
We are presenting a new functionality that will help to get visibility on the vulnerabilities affecting a specific asset in your inventory.
The new Security Insights tab available in the asset details will allow you to quickly understand the security threads for any relevant asset.
Also, it improves the flow to drill down from a vulnerability to an associated asset and vice versa.
To get more detail on how to use it, visit the following KB article:
https://community.lansweeper.com/t5/cloud/viewing-the-vulnerabilities-affecting-assets/ta-p/64846
Remember to write a comment with any feedback for our vulnerabilities module or just to say how much you like it 😉 !
Thanks.
- Labels:
-
Vulnerability Risk Assessment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 07:41 PM
is there a way to remove non active devices from the Asset part of the summary? I have assets that have not been scanned since 2021 and locally are not active we are just maintaining a history of them for now but it seems to be messing up my count in this new app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2022 10:09 AM
Hi @Michaelzip0,
That will be possible when we release the custom views with advanced filtering, expected in Q1'23.
It was already commented in the following post:
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2023 10:29 AM
Hi @edu_ayus, is this already possible today to filter the non active devices from the Asset part of the summary?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2023 09:53 AM
Hi @FGF358 and @Michaelzip0,
Filter vulnerabilities by asset state was enabled back in January thanks to the functions that enable customizable views.
How to apply this filter?
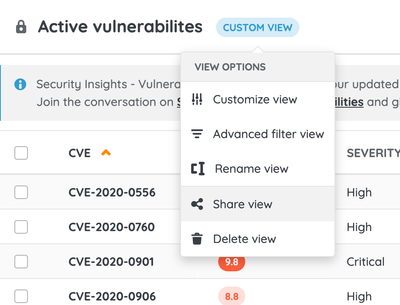
1. Open the advanced filter's configuration modal from the Active vulnerabilities view. You can do this from:
- The action area of the left menu (under the "Customize view" action).
- The button to the right of the local search engine in the upper right corner.
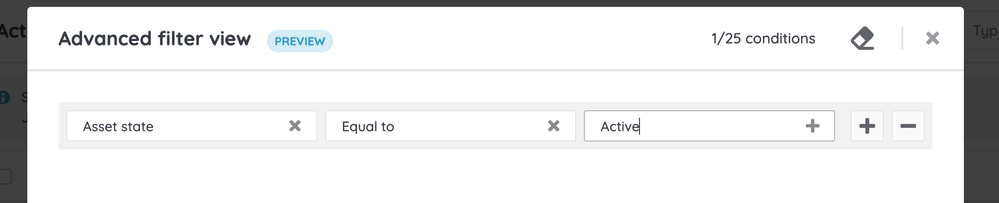
2. Configure your filter criteria:
- Choose the "Asset state" field in the first field dropdown.
- As the operator, select "Equal to".
- Select the asset status value you want to filter by, which is most likely "Active".
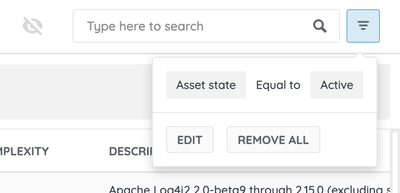
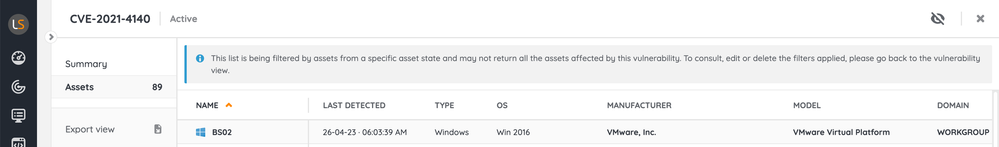
3. Apply the filter by clicking on the "Apply" button in the modal's footer. The system will apply the filtering instantly, and you will notice how the counters of how many assets are affected by each vulnerability may have changed. Quickly hover over the advanced filters button in the upper right corner to remember the filter criteria applied.
4. To see the list of vulnerable assets filtered by the selected asset state, click on the vulnerability that interests you from the "Assets" column. An informative banner will remind you that the listing is being affected by a filter.
Bonus tips:
1. You can export the list of assets affected by a vulnerability filtered by an asset state at this time using the "Export view" action that you will find in the left menu.
2. If the query for vulnerabilities affecting only assets of a specific state will be recurring, save your custom view privately to return to it quickly and save time on future occasions.
3. Once the view is saved, you can share it with all or some of your team members.
I hope this information helps you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 04:25 PM
Hi @Hendrik_VE,
- Thanks for the feedback, it is concrete, and it has value for us. I totally agree with it, as I also consider providing visibility of the element in the asset (HW/OS/SW) causing the vulnerability saves time for users pointing them to the key component to review. In fact, I am glad to say this is already in our backlog, and it will become part of Sec. Insights in the coming months. Confirming with messages like yours it will be helpful for users is very nice.
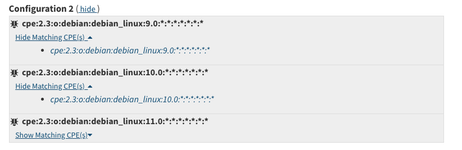
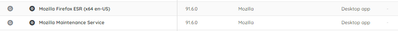
- I reviewed the CVE from your post and it is true Mozilla Firefox ESR is supposed to be fixed with versions >91.3. I see two options two validate:
- There is no other Firefox distribution installed on the machine (which needs versions >94.0
- There is a second configuration described on the CVE, related to the Debian distribution, maybe it could apply
Once we introduce the functionality described above, it will avoid doing this validation. 🙂
Thanks again for the post, and I hope to see more feedback coming from you. I would also be happy to have a call to continue discussing about Security Insights, just let me know if you are interested.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 01:05 PM
Nice addition. Two remarks though:
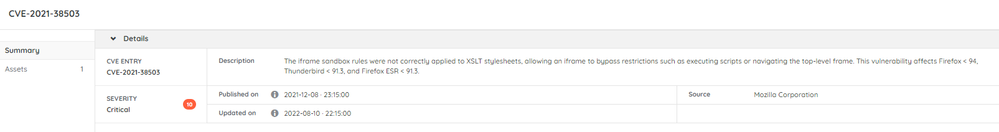
- It would be much more useful if it would also point to the vulnerable component in the asset. For instance, the first asset I look at shows a critical (10 score) vulnerability:
It doesn't tell me where it comes from (in my case I guess it comes from a Mozilla Firefox installation). It would become interesting if you could click on the vulnerability and from there open up a page/get a pop up displaying the affected software/hardware component.
- The CVE tells me the vulnerability is solved in Firefox >91.3 (I have 91.6), so it seems I'm not affected and it's giving me a false sense of insecurity. In order to use the Security Insights module, it's importing that it's giving accurate information.
Product Discussions
Share feedback, exchange ideas and find answers to Lansweeper product questions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now- Group vulnerabilities by affected product in Reports & Analytics
- Enhance Security and Compliance with Lansweeper's Free Database Scanner in Product Announcements
- What's New? Lansweeper Summer Launch 2024 in Product Announcements
- Risk Insights - Vulnerability report for most affected assets in Product Discussions
- Customising vulnerability views. Did you know these tips? in Product Discussions